Protecting private and sensitive data information
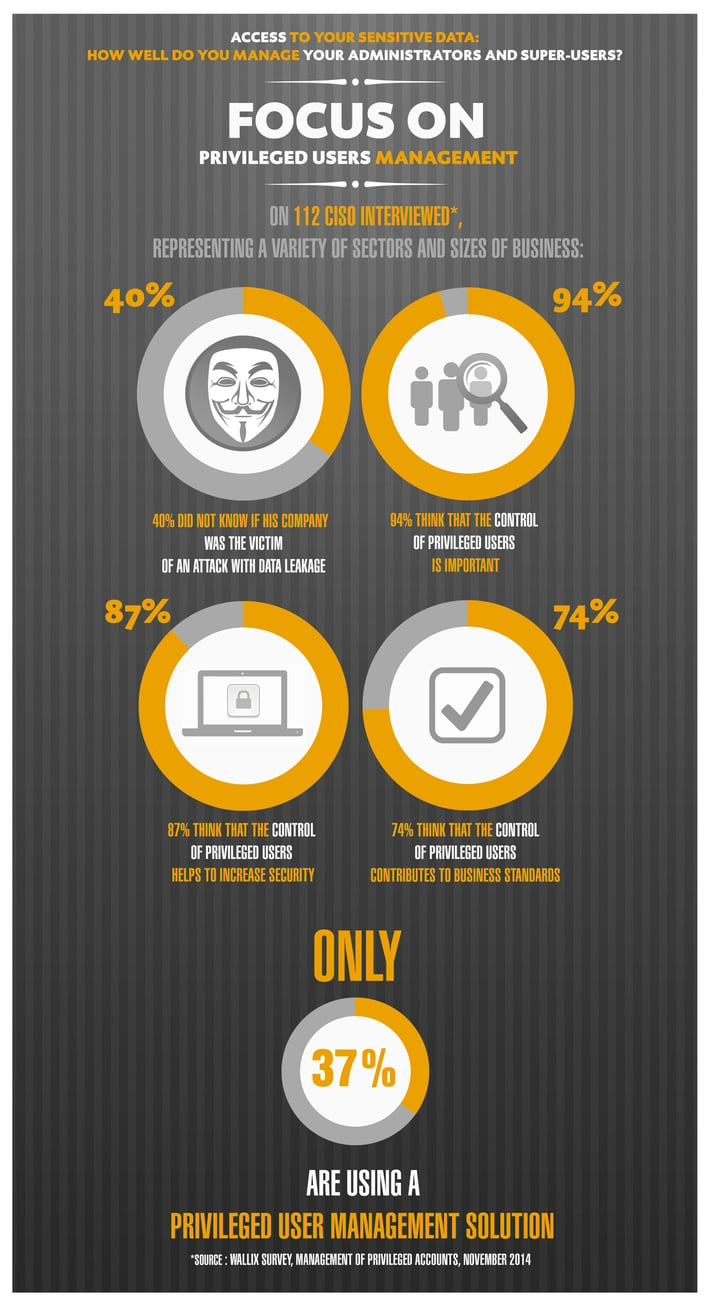
Today, are there established ways to protect private and sensitive data information within operating systems or IT hosting services? The recent survey conducted by Wallix reveals that 94% of interviewed CISOs believe that controlling privilieged users' access to sentive data information is important, or very important. Equally, 87% hold the idea that privileged user management solutions contribute to overall IT security reinforcement through compliance.
However, only 37% of CISOs actually use a privilieged access management solution.
Clearly today, as cloud technologies and big data are strongly developing and while digital transformation is spreading globally, permiter security systems are becoming less protective of sensitive information. Now, cyber threats have migrated from the outside to the inside, making internal users organizations' biggest threats because benefiting from privileged access to their most vulnerable information.
An increasing portion of data thefts or data leaks now comes from fraudulent uses, malwares, or security incidents, all of which are linked to privileged user accounts. That means that securing privileged access, managing passwords, and tracing connections should be at the heart of CISO' security policies.
Managers' responsibility towards sensitive data information protection plays therefore a crucial role and needs to lead them to determine priorities in terms of IT budgets and investments. There is still time to tackle IT security risks management issues and align IT budgets with CISO' s priorities.
And managing privileged user accounts seems to be at the top of them all.
To get more information about this topic, download Wallix's market study for free or this white paper.




