Privileged Access Management Best Practices
Privileged access management (PAM) is imperative in protecting critical systems and data. Organizations can’t just rely on perimeter-based defenses; instead, they must maintain complete control and visibility over privileged users and their access to various resources to ensure security.
The estimated cost of an average data breach is $3.8 million.
Having a PAM solution in place is the first step to protecting your organization, but if you don’t follow some privileged access management best practices, your organization could still be vulnerable to attack. Maximize your investment in a robust PAM solution like WALLIX by following these privileged access management best practices.
Without implementing privileged access management best practices, investing in PAM is a waste.
Benefits of Privileged Access Management
First of all, why would you want a privileged access management solution at all? With security infrastructure like SIEMs and IDS in place, isn’t PAM simply extraneous? – No! Privileged access management helps organizations get the most out of their existing investments in security infrastructure.
Privileged access management helps enterprises:
- Control and monitor the actions of privileged users.
- Secure passwords that enable the connection of target appliances with a centralized password vault.
- Create a clear picture of who has been granted access to networks and sensitive equipment.
- Patch potential security vulnerabilities caused by oversight.
- Apply a granular user connection policy and create a centralized overview of service providers and their access privileges.
- Secure remote access by defining rules that allow for the automatic authentication and revocation of access rights in a given period.
- Log all sessions as soon as service providers have access to target resources.
- View user activity in real-time.
- Maintain detailed audits that can be compiled from metadata feeds in dashboards and produce context-relevant reports.
- Record and replays users’ sessions, allowing you to attribute all connections and access to specific user sessions.
Privileged Access Management Best Practices: Preparing Your Enterprise
Get ready for deployment (or maximize the benefits of an existing deployment) by taking these preparatory steps.
1. Identify and Prioritize Risks
First, gather information about how current privileged accounts are being used and managed within your organization. This will help you understand where your security infrastructure is lacking.
First, organizations must address the current state of their security infrastructure.
After gathering this information, you may realize that you can’t centralize all systems into a PAM solution right away – that is okay. Determining your most critical and sensitive business systems and data, and securing those is a good first step to ensuring complete enterprise security.
2. Address Shared Accounts and Passwords
Many organizations use shared accounts and passwords to simplify system access management. Unfortunately, this leaves your organization extremely vulnerable to attack, both from insiders and outsiders. With no clear break down of who has access to what, your potential attack surface area significantly increases.
Shared accounts and passwords significantly increase the attack surface of your organization.
Privileged access management provides an easy solution to this problem by limiting users to access only those systems that they need with minimal privileges to get their required jobs done. Users log in with local system or administrative accounts without using root passwords. Instead, they log in via a Bastion where actual root passwords are protected and encrypted in a centralized password vault and never revealed to end users. This means that users cannot bypass the PAM solution by logging directly into devices or applications.
Privileged Access Management Best Practices: Permissions
Without clear visibility over who has access to various resources in your organization, you don’t have complete control.
3. Streamline Privileges
To ensure complete security within your organization, it is best that all users operate using the least amount of privileges necessary to complete their job. Over time, a variety of users may have been given access to sensitive resources and never had those permissions revoked, even if they no longer need access. This could lead to a data breach if the person has malicious intentions or if their credentials are compromised by an outsider.
Give users the minimum permissions necessary they need to complete their job duties.
It’s not a question of trust. Unused or un-needed credentials are simply an unnecessary risk. Streamlining security by removing users who no longer need access or haven’t used those resources in a long time also makes it easier for system admins to have a clear view of who has access to resources within an organization.
4. Utilizing Automation and Self Service Features
Streamlining privileges may result in users not having access to the data they need to complete a project. Rather than having to manually address access requests, privileged access management allows you to utilize a self-serve automated permissions platform.
Users can easily request and be granted access to the resources they need. Administrators can grant unlimited access or grant one-off permissions for a specific period of time. This helps keep credentialing streamlined even as access controls are tightened.
Secure Access = The Only Access
To truly enforce your security infrastructure, you need to make sure that secured access is the only access into systems. It is important that other remote access methods are closed off to ensure that all actions can be monitored by your PAM solution and that you maintain complete visibility. This type of one-way-in and one-way-out mentality can be enforced by utilizing other aspects of your security infrastructure, like a firewall.
Not completely eliminating other forms of remote access is like locking the front door of your house and leaving the back door wide open.
Privileged Access Management Best Practices: Heightened Security
Protecting your most critical systems and data should be a top priority for organizations, even if implementing the other aspects of PAM take a little more time.
5. Take Extra Measures to Defend High Priority Systems
Privileged access management makes it easy to control and manage access as well as monitor and record sessions for audit and compliance regulations. However, many organizations take extra precautionary measures to protect their most critical systems and data.
Consider only allowing one-off access for everyone looking to access these important resources. You can even go one step further by setting up automatic alerts for every time someone accesses these systems so security operations teams can monitor the actions of those users in real-time.
6. Continuously Monitor
The fact is, no security operations team will be able to watch every single user in real-time all the time, so you want a tool that can record all actions for future review. This information can be particularly useful for going back to find the source of a data breach. In addition, this data can be used to understand how privileged access is being used by internal and external users to inform future security policies and procedures. Plus, users simply knowing they are being watched can significantly deter them from taking malicious or careless actions.
Unalterable audit trails make it easy for organizations to review the actions of privileged users and meet compliance regulations.
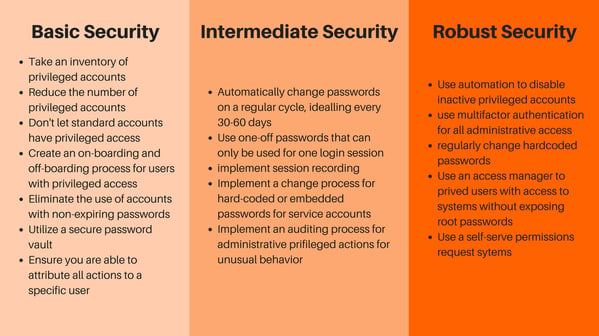
Privileged Access Management Best Practices: Action Items
By taking the following actions, you can quickly elevate your organization’s security from basic to robust.
The WALLIX solution provides your organization with a PAM system that helps you meet the criteria for all privileged access management best practices. Our solution includes:
- Access Manager: Provides users with a single point of access to all systems and data. Super administrators can grant or take away access to various resources as necessary.
- Password Vault: Encrypts and secures all passwords in a centralized vault that removes the need for users to have root access to critical systems, further protecting your enterprise.
- Session Manager: Tracks and monitors the actions of all privileged users within your organization with unalterable audit trails that can be used for future review and to meet compliance regulations.
All of these tools are centralized within a single interface that can integrate with your existing security infrastructure. The WALLIX solution provides an easy way for IT administrators to monitor all activity and look out for potential breaches in real-time. Plus, unalterable audit trails make it easy to meet compliance regulations and allow security teams to review sessions in case of a breach. Protect your organization from internal and external threats with privileged access management from WALLIX.
Privileged access management from WALLIX makes it easy to monitor, manage, and audit all privileged accounts.
Interested in scheduling a demo of our solution? Request a live demo now!

