It can be daunting to manage security for privileged accounts. You demand system security while administrators go about their work of changing configurations, installing software, changing user accounts and so forth. But, chances are, you have a diverse collection of systems, each with its distinctive pattern of root access privileges.
Preventing Data Breaches or System Outages
Your goal is to prevent accidental data breaches or system outages. You also want to protect yourself from malicious acts. At the same time, there are forces arrayed against you. Think of it as a triangular set of opposing energies. As the figure suggests, you can be thrown off of your goal of effective, secure Privileged Account Management (PAM) by the need for consistency, flexibility and economy. You want PAM without running your bank account dry or imposing draconian policies that inhibit flexibility and invite circumvention. What is to be done?
Send in the Army?
One solution is to invite a small army of consultants into your IT department to make PAM happen. (Even if it is, as the US Army used to call itself, “An Army of One,” it can still feel like an invasion.) There are some benefits to this approach. Consultants generally come equipped with specialized knowledge that your team may lack. They are hired specifically for PAM, a duty that your regular staff may not have the time to address. However, for a variety of reasons, you should consider the alternative of investing in easy to use PAM software instead.
Don’t confuse audit with accuracy
An audit of privileged account policies and access logs may be useful but it won’t get you very far if you want complete control over PAM. Auditors spot check logs and review written policies. They search for anomalies in account access log records and flag questionable sessions. The problem with this is that they can miss a great deal in the process. (And it’s not a cheap process). What’s more, audits only look in the past.
An effective and easy to use PAM solution like the Wallix AdminBastion (WAB), gives you control of privileged account access in real time. You will know which systems are protected by PAM and which are not. You will know who has access. You will be confident that ex-employees are shut out of privileged systems – and that no individual will have actual device passwords.
Think about what happens after the consultants leave
When that army of consultants leaves, you still may not have a clear idea of what’s going on with PAM. For instance, consultants may set up a combination of custom PAM solutions and policy. With that approach, you may lose control of PAM as time goes on. Or, worse, you may not even know that you’ve lost control. That’s why it’s so important to have an off-the-shelf solution that you can understand, operate, and keep up-to-date.
Consultants are expensive.
Consultants may seem inexpensive compared to an investment in software, but you invariably need the consultants to return again and again. The consulting fees will quickly outrun the price you would pay for software licenses and maintenance. The table below compares a $10,000 investment in PAM software with a consulting-based approach to PAM. With an internal resource spending 10 hours a week on PAM and 18% annual maintenance, the software approach is still significantly less expensive than having a $200 per hour consultant on site for 200 hours a year. Over a 5-year period, the consultants will cost $90,000 more than the software investment.
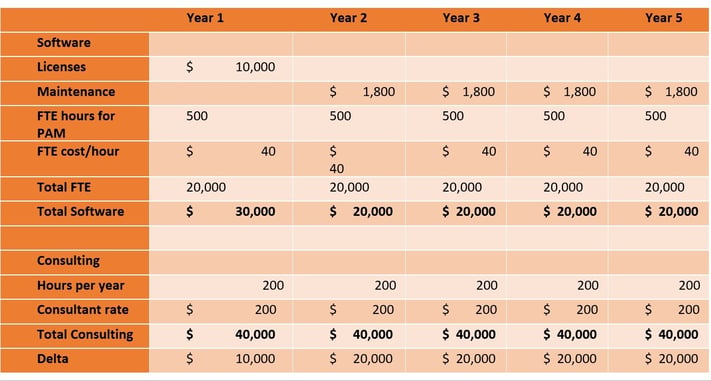
Note: Information is for informational purposes only, based on industry average metrics.
An off-the-shelf-solution that ALSO requires an army of professional services to deploy and keep running (and all-too-common occurrence) is the worst of all worlds.
Know what people are ACTUALLY doing
Written policies are fine, but do you want to know what your people are actually doing in their privileged account sessions? WAB records privileged sessions with video replay. You can see exactly what an administrator did, or didn’t do, after the fact. This can be extremely useful in diagnosing what led to an outage or data breach.
Be both « us » and « them »
Despite the best of intentions, bringing in consultants may lead to a negative « us vs. them » dynamic with the IT department. Thought of as the PAM « cops », the consultant’s efficacy may suffer as a result. You may get a handoff of policies that are not followed closely after the consultant leaves. By investing in software and empowering your own team members to do PAM, you get the best of being both us and them – you have the power and capabilities of « them » but the inclusiveness and cooperation of « us ».
The Wallix AdminBastion
The Wallix AdminBastion (WAB) is a tool that helps mitigate the risk security incidents that arise from PAM problems. It’s a driver of cost savings all around. WAB creates a single gateway with single sign-on for access by system admins. This capability enables the IT department to define and enforce access policies for admins as well as for the employees who need system access.
WAB’s agent-less architecture is lightweight, making the solution inexpensive and easy to deploy and adapt. Many PAM solutions require a dedicated software agent on each administered device or workstation. This need inevitably creates costs by slowing down deployment, management and adoption. If agents do not cooperate in system change cycles, PAM may be ignored or circumvented. Errors and fraud flourish in organizations where PAM has been side-lined like this. Administrative overrides, direct local access to servers and shared passwords give malicious actors a fertile breeding ground. WAB gives you the tools to prevent these potentialities.
For more information about the Wallix AdminBastion, visit www.wallix.com/ or click below.





