An IT security professional recently asked me this question. As I began to research opinions and marketing messages it became more clear to me that many in the IT security industry are keen for us to separate the risks posed by a malicious outsider from the exposure created by privileged accounts on the inside of an organization. The aim of every malicious outsider is to ultimately become a privileged insider.
As an example, if you take the view that a particular server on a network doesn’t need securing or monitoring because it’s only used by one individual inside my company, you potentially fail to understand the nature of external threats. There is increasingly large investment being made in perimeter defences and detection of advanced external threats, which is a good thing. But these kinds of threats whether targeted malware or exploits rely on the ability to “escalate privilege” once inside and that means we must take as seriously the security of accounts used by privileged insiders.
One perfect example of this “lateral movement” by hackers once inside a network was the Sony Pictures breach. They had failed to secure accounts with elevated privileges which made it easy for the malicious outsiders to become privileged insiders finding and removing the data they wanted.
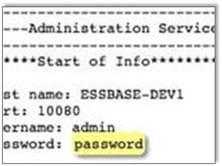
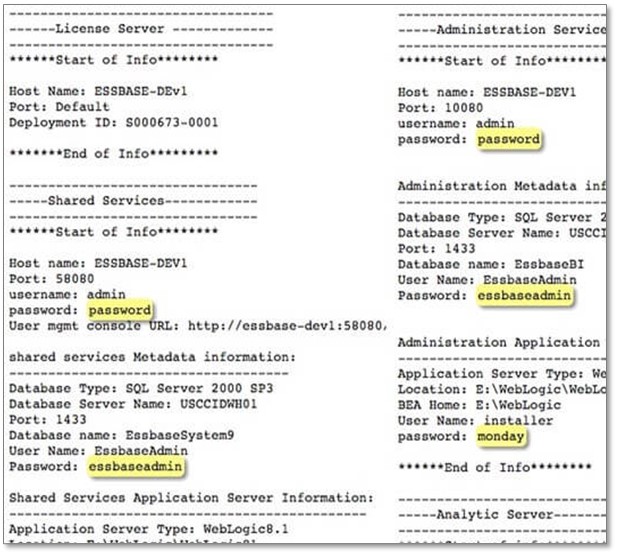
How could this be possible? Documents collected during the hack have now been indexed by Wikileaks and give us a good insight into some of the poor management of potentially privileged accounts that might have given malicious outsiders their opportunity. In this excerpt you can see a whole set of IT assets and the accompanying user names and passwords.
I also highlighted in a previous posting how the impact of vulnerabilities like VENOM could largely be neutralised by having a better grip on privileged accounts. Addressing the challenge of privileged access doesn’t need to be complex or expensive and could begin to play a critical role in your IT security strategy. You can find out more about how Wallix can help deliver agentless and easy privileged user management on our website.





