Privileged Access Management (PAM) is usually discussed in the contexts of IT or information security. This makes sense. Precise, auditable management of information systems access is an inherently technical matter.
However, PAM is also very much an organizational issue. It’s people who use systems. It’s people who misuse systems, either deliberately or by mistake. And of course, ultimately it’s bad people posing as good people who can truly wreak havoc on systems when they steal privileged credentials.
Achieving the best security and compliance results with PAM requires thinking about how access privileges align with your organization.
Privileged Access Management and Process
Consider the following simplified example of how people interact with information systems: The workflow shown below represents a typical procurement process. Operations needs something procured so they issue a purchase order (PO). An Operations Manager’s approval is needed for the PO to be valid. A Procurement Clerk sources the goods and his or her manager approves the purchase. Procurement requests payment. A Payables Clerk prepares the payment and the Payables Manager approves it.
Why are there so many steps and people involved in this seemingly minor transaction? The answer is that most well-run businesses have what are known as “internal controls” to protect their finances from errors and fraud. Money is never spent without management approval. Purchases are not made without a purchase order, and so forth. Without these controls, a business could easily spend money without knowing it or accidentally expose itself to fraud.
As a further control, this business engages in the practice of “segregation of duties,” which is required through the COSO control framework used in Sarbanes Oxley compliance. The segregation of duties sets a policy that no one individual can both request and authorize a payment. For example, the Procurement Clerk should not be able to request and then approve payment to a vendor. If this were possible, the company is vulnerable to fraud or errors. A parallel control might prevent a single person from approving a new vendor and then approving a payment to that vendor.
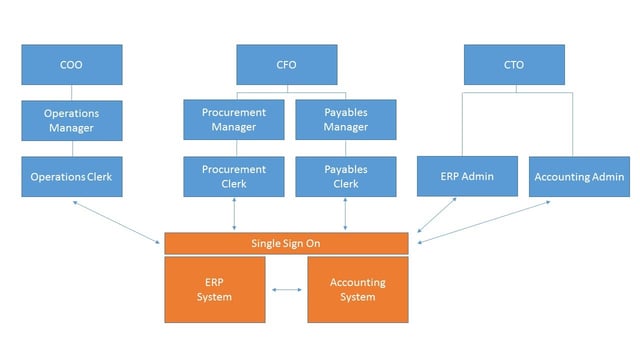
So far, so good. Now, think about how the approval workflow and segregation of duties control are actually realized through information systems in real life. The figure shows a simple rendering of the three organizational stacks that realize the procurement workflow through access to the enterprise resource planning (ERP) and accounting systems. Each participant in the workflow has a distinct set of access privileges to the respective systems. For instance, the Payables Clerk cannot access the “Create PO” functionality on the ERP system. The Operations Clerk cannot access the “Approve Payment” function. The various managers may have overrides that enable them to cancel payment authorizations and so forth, but the people who report to them should not have this ability.
The access privileges management of these controls is potentially messy. The IT organization must understand the workflow and its relationship to the procurement and finance organizational structures. Whoever implements the access privileges has to understand the intent of the controls. This is already potentially challenging, as IT staffers may not have a great sense of accounting controls. Furthermore, the procurement workflow is just one of perhaps hundreds of controlled workflows. Keeping up with the privileges will be difficult. Factor in people moving in and out of jobs, corporate restructuring and systemic changes and the process of managing access privileges becomes all the more stressful. If it is done manually, it is virtually guaranteed to be deficient.
Privileged Access Management to the Rescue!
First, it is imperative to invest some resources in making everyone more aware of how controls, compliance and security actually work. Business people need to have a healthy understanding of how their access to information systems affects security and compliance. Conversely, IT people must develop a strong sense of how their work relates to the secure fulfilment of business workflows. It is not wise to assume that all employees already know how software and security work. They don’t.
Second, a Privileged Access Management (PAM) solution has the ability to manage access rights across the full business organization and up and down the IT department org chart. The Wallix AdminBastion (WAB), for example, creates a single gateway with single sign-on for access by system admins. This capability enables the IT department to define and enforce access policies for admins as well as for the employees who need system access. WAB lets admins manage access rights and passwords to servers and other devices through a single console. This setup enables the IT department to adapt access privileges quickly in response to organizational change. IT department turnover also becomes less of an issue with this level of control, ensuring that critical servers cannot be accessed by individuals no longer authorized to do so.
WAB’s agent-less architecture is lightweight, making the solution easy to deploy and adapt. Many PAM solutions require a dedicated software agent on each administered device or workstation. This need inevitably slows down deployment, management and adoption. If agents do not cooperate in system change cycles, PAM may be ignored or circumvented. Errors and fraud flourish in organizations where PAM has been side-lined like this. Administrative overrides, direct local access to servers and shared passwords give malicious actors a fertile breeding ground.
The combination of increased awareness of access privileges and an automated PAM solution will bring the organization and privileged access management into better alignment. Successful organizational-PAM alignment, which improves security and compliance, comes from selecting a PAM solution that is easy to deploy and flexible enough to adapt to the inevitable cycles of change that sweep across all organizations. Wallix AdminBastion has been proven to deliver on these important fronts.
What should you expect from a PAM solution? Read our free eBook:





