The Book of Ecclesiastes reads, “Using a dull ax requires great strength, so sharpen the blade. That's the value of wisdom; it helps you succeed.” (10:10) And it may as well work for information security as InfoSec seems to have many areas of practice where we’re busy cutting down trees with dull axes.
We forget that sharpening our tools might make our lives easier.

Using Secure Socket Layer (SSL) to manage privileged accounts offers one such example. There’s nothing wrong with SSL and SSL Virtual Private Networks (VPNs). It’s just not an efficient approach to Privileged Account Management (PAM). Let’s explore why SSL VPNs results in hidden costs for PAM.
A Quick Check In – What’s PAM?
PAM, which also sometimes stands for Privileged Access Management, deals with authorizing and monitoring privileged users, the people who have administrative access to critical systems. Privileged (or “root”) users can modify system configurations, add and edit accounts. A PAM solution grants, revokes and tracks privileged access based on IT department needs and organizational policies.
The SSL Approach to PAM
SSL VPNs, depicted in simple form in Figure 1, utilize a Certificate Authority (CA) to give remote users access credentials. A CA server issues a certificate (a unique, self-expiring piece of code) that entitles the remote user to log into internal systems. SSL VPNs typically allow access for a single system, not the entire network.
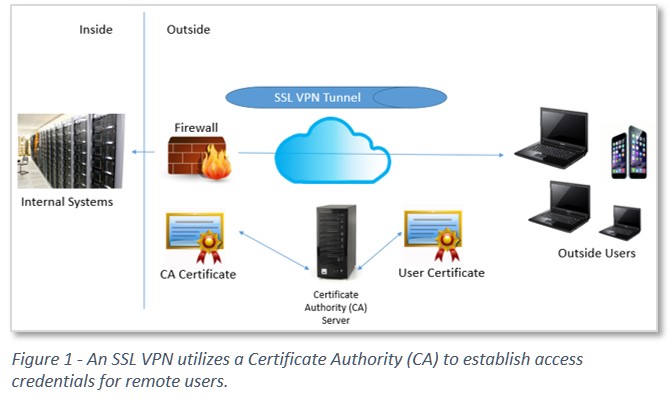
A privileged user outside the firewall could use the SSL VPN to gain administrative access to a system. This is a common need. Many privileged users are remote: Vendors, third party managed services providers and offshore teams are just a few examples of possible external privileged users.
Relying on an SSL VPN to do privileged account management can pile up unproductive and costly administrative time:
- There are a lot of moving parts to manage – An SSL VPN approach to PAM involves managing a firewall, a CA server and an identity store. The identity store (e.g. LDAP) has to be configured to support privileged access rights. For example, if John Doe has admin access to the email server, that fact needs to be reflected in his identity profile. As access rights change, and they frequently do, the store needs to be kept up to date.
- Reporting requires collating data from multiple systems – A number of stakeholders need to see reporting related to PAM. These include security and compliance managers as well as outside auditors. It’s a time-consuming chore, however, to pull together and correlate data from the firewall, CA server and identity store.
- The identity store and CA need to track third party employees – Most, if not all remote privileged users work for someone else. Modifying an identity store every time a vendor adds or terminates an employee creates a time-consuming, error-prone work load.
The PAM Portal Alternative
New approaches to PAM, such as the Wallix AdminBastion Suite (WAB Suite), offer a streamlined portal architecture to manage privileged access. As shown in Figure 2, WAB Suite combines all of the functions needed for PAM into a single solution.
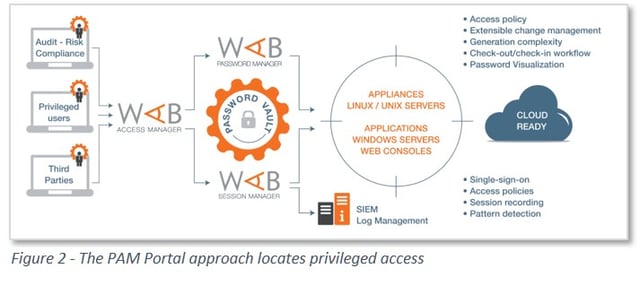
At the front end, privileged users sign in to an Access Manager through a portal. All privileged users are alike. They all have to go through the same Access Manager. The Access Manager stands as a single point of policy definition and policy enforcement for PAM. The Access Manager knows which systems the user can access and at what level of privilege. A super admin can add/modify/delete privileged user accounts on the Access Manager. This approach reduces the risk that a former employee will retain access to a critical system.
Compared to the SSL VPN approach to PAM, the WAB Suite portal-based PAM solution offers a number of security and cost benefits:
- A centralized, unified system for all PAM – WAB enables quick management of access across a disparate set of heterogeneous systems. Management of the PAM solution should be far less taxing on IT resources than the SSL VPN approach.
- Reduced risk of unauthorized access – The best PAM systems prevent privileged users from knowing the actual passwords to critical systems. The goal is to prevent a manual override on a physical device, for example. WAB keeps passwords in a secure vault and gives the privileged user access once he has cleared the Access Manager.
- Better awareness of privileged account use - WAB’s Session Manager records what privileged users actually do during their administrative sessions. Audit reporting is more streamlined and integrated than the equivalent process with SSL VPN.
- Easy to deploy – WAB is simple and efficient to set up and maintain. With cloud-hosted options, implementation is quite fast. WAB is able to work with virtually any privileged account, including those required by platforms that manage mobile devices and the like. WAB’s Agent-less deployment - WAB doesn’t force the IT department to install special software on every system where they are managing privileged access.
With the new, portal-based approach to PAM, there can be one less dull axe at work in the IT department. Even though Solomon also wrote “There is nothing new under the sun,” perhaps he didn’t know about WAB Suite.





