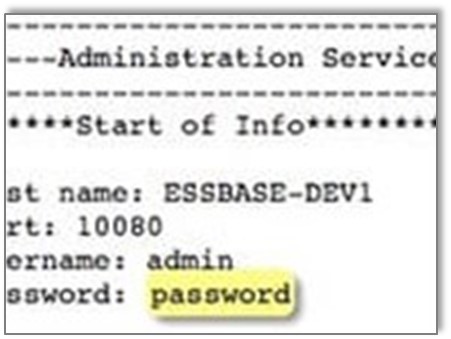
An IT security professional recently asked me this question. As I began to research opinions and marketing messages it became more clear to me that many in the IT security industry are keen for us to separate the risks posed by a malicious outsider from the exposure created by privileged accounts on the inside of an organization.
WALLIX
Recent Posts
What's the aim of every malicious outsider?
[fa icon="calendar'] Jun 29, 2015 1:21:45 PM / by WALLIX posted in Reaching IT Compliance
IT Security: 5 things we learnt at Infosecurity Europe
[fa icon="calendar'] Jun 18, 2015 12:30:00 PM / by WALLIX posted in Mitigating External Attacks
Well it was that time of year again, except it wasn’t, as Infosec moved from its traditional home at Earls Court to Olympia at the start of June instead of April. The exhibition floor itself had a different feel about it too with that big glass ceiling pouring in natural light.
CISOs: “Privileged access is the beast we still haven’t tamed”
[fa icon="calendar'] Jun 11, 2015 11:24:00 AM / by WALLIX posted in Mitigating External Attacks
This week I was fortunate enough to be able to attend the IT Security Guru’s annual Analyst and CISO Forum here in London. A gathering of the great and the good from the analyst community and some cutting edge vendors were part of what proved to be a fascinating roundtable with 10 of the UKs top CISOs.
Is the VENOM vulnerability really a cloud armageddon?
[fa icon="calendar'] May 27, 2015 2:25:00 PM / by WALLIX
When it comes to media coverage of IT security issues there is occasionally a tendency to over-state the risk. Headline writers take there opportunity to exploit (pardon the pun!) our lack of technical expertise to paint scenarios of impending doom.
Are disruptive technologies breaking PCI compliance?
[fa icon="calendar'] May 14, 2015 11:27:00 AM / by WALLIX posted in Mitigating External Attacks
Today more than two thirds of all payment transactions will use a card, meaning around $20 trillion in purchases will be on plastic by the end of 2015. This makes security an increasing priority for any business that handles card payments and data.