Because cyberthreats to data and privacy are ubiquitous, cybersecurity needs to be a part of every corporate network – and of course, protecting the personal, financial, health, and other data held by corporations is of paramount importance. Aside from the loss of the data itself, though, executives must also contend with another serious issue: The financial costs of a data breach, in terms of both damage mitigation and the penalties that will be assessed by various governing agencies should the company not have been compliant with appropriate regulations and laws.
Legacy Obstacles to Access Management
The extent to which business still runs on outdated tech might surprise you. Banks and other fintech companies, for example, still lean heavily on mainframes and other so-called “big iron” infrastructure because of its speed and reliability in handling thousands of transactions per second. Those kinds of capabilities beg the question as to whether such tech is indeed outdated – but legacy tech designed for high throughput does pose problems, with a high number of administrators citing integration with legacy systems as a challenge as they consider future planning and efforts.
Transforming Data into Knowledge: Top 5 WALLIX Webinars
Our modern, connected society generates vast amounts of information -- by some estimates, over 90% of the data extant in the world was created over the last two years. And with the right systems in place, data turns into information that drives business intelligence and enables insightful decision-making. The uses are as endless as the data itself, enabling everything from ad targeting to Smart Cities, and transforming entire industries on the fly.
Privileges, Not Rights: Keeping Control with Privileged Access Management
Business has always run on personal connections. But for many years, it’s also been run on a host of network and data connections designed to provide both internal and external users with the access to corporate systems and information that they need and want. On a daily basis, millions of workers use that access to do their jobs – and they take that access for granted, in large part because of the relative ease in accomplishing it. But there’s a facet to this access that should always be kept in mind, both by users of networks and the administrators charged with protecting those same networks and data: Access is a privilege, and not a right.
The Worrying Rise of Healthcare Data Breaches
Last year was not a good one for the healthcare industry’s security reputation. A quick Google search will unearth countless news articles focused on data breaches in healthcare from across the globe. In the UK, cyber attacks and data breaches hit the NHS hard, while private healthcare providers in the US, UK and Australia all suffered at the hands of hackers.
3 Questions CISOs Should Really Be Asking
The key objective of any CISO (Chief Information Security Officer) is the prevention of impact to the organization from any form of security breach. This, as we know, is much easier said than done. A good CISO, in fact, comes to work every morning assuming that a breach has already happened, with a view to fixing any vulnerabilities and securing the system to the highest standard possible. Every single day.
Cybersecurity Simplified: Bastion Managed Services
Who better than WALLIX to manage your Bastion?
Privileged Access Management (PAM) is recognized as a critical system for the Digital Transformation, allowing organizations to ensure the security of their critical accounts, as well as assisting in complying with required regulations. In fact, Gartner named PAM as the #1 cybersecurity priority for businesses - 2 years running.
What is the Principle of Least Privilege and How Do You Implement It?
In the military, they have a well-known phrase that happens to succinctly describe the definition of the least privilege principle: ‘Need-To-Know Basis’. For the military, this means that sensitive information is only given to those who need that information to perform their duty. In cybersecurity, it’s much the same idea. The ‘least privilege’ principle involves the restriction of individual user access rights within a company to only those which are necessary in order for them to do their job. By the same token, each system process, device, and application should be granted the least authority necessary, to avoid compromising privileged information.
2018 Breaches: How PAM Could Have Helped Prevent the Worst of Them
There have been quite a few security breaches to hit the news in 2018. As each story broke, it seemed like it couldn't get worse, only to find that the next data breach was just around the corner, and even more severe, exposing the data of millions of customers worldwide. We have had a few of those this year.
WALLIX is positioned in Gartner’s first Magic Quadrant for PAM
WALLIX is positioned in Gartner’s first Magic Quadrant for Privileged Access Management (PAM)
Securing DevOps in the Cloud with Privileged Access Management (PAM)
A recent cybersecurity news item should trigger concern for anyone involved in cloud-based software development. As reported in CSO, an attacker breached a popular Node.js module. After building trust and gaining owner-level access, he or she was able to push a compromised version that hid Bitcoin and Ethereum hot wallet credentials for malicious purposes in the code.
Utilizing Privileged Access Management (PAM) to Combat Multi-Tenant Environment Risks
Multi-tenancy, which involves the sharing of infrastructure, software, and network assets by more than one entity, is the predominant mode of computing in the cloud. There are good reasons for this. A multi-tenant environment is more efficient than alternative approaches like assigning each system its own individual machine. Cloud Service Providers (CSPs) host multiple companies' IT resources at once, providing each with cost savings compared to self-hosting all resources on-premise.
PAM | Securing the Cloud
Organizations are flocking to the cloud in droves, but many question the security of migrating critical resources to off-site, cloud services. In fact, Forrester reports that 58% of companies outsource half or more of their data center operations, servers, network, and storage infrastructure!
The Forrester Wave™ | WALLIX Recognized Among Top PIM Vendors
WALLIX makes its debut in The Forrester Wave™: Privileged Identity Management, Q4 2018, which evaluated the “11 providers that matter most.”
Utilizing Session Management for Privileged Account Monitoring
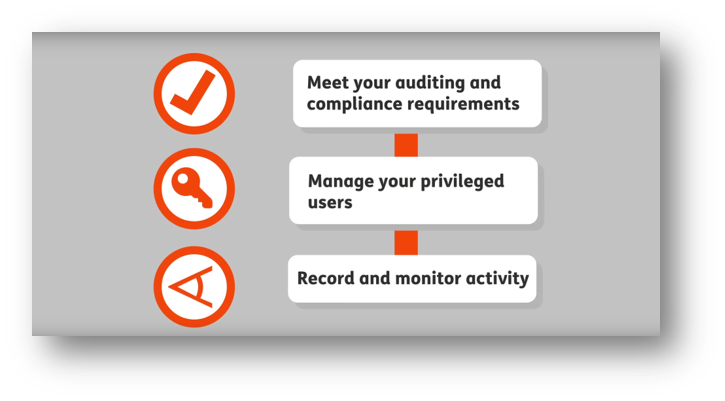
Maintaining visibility and protecting an organization’s most critical data and systems are central components of robust security operations. Privileged users present a unique risk to companies, whose credentials may get into the wrong hands, resulting in devastating consequences. To maintain the level of visibility and control required for numerous compliance regulations, many organizations look toward session management solutions to provide them with the tools they need to ensure proper security 24/7.
What is PAM? | Privileged Access Management
Privileged access management, or PAM, is software that helps organizations maintain complete control and visibility over their most critical systems and data. A robust PAM solution ensures that all user actions, including those taken by privileged users, are monitored and can be audited in case of a security breach.
Why Privileged Account Security Should Be Your #1 Priority
When you return one day to find your house has been broken into, your first question is always, “How did they get in?” And when the doors and windows are all still closed, yet your valuables are gone, you’re sure those things didn’t just walk off on their own. Similarly, in the event of a data breach, your first question is inevitably, “How did this happen?”
Bring a Privileged Access Management Policy to Life
There’s a misconception in the popular imagination that cybersecurity is a technology-driven discipline. It is technological, of course, but cybersecurity policies are arguably just as important, if not more so, than the hardware and software elements they govern. Policies, or rules, determine how security technology is to be deployed by affected teams. A firewall may prevent unauthorized entry, for instance, but it is useless if there are no rules governing who is allowed to modify its settings.
Enterprise Password Management Software: WALLIX Bastion Password Manager
Organizational security often begins with password management. Even the most basic of organizations use passwords to protect email accounts and document management solutions, while larger organizations may need to worry about HIPAA compliance, protecting industrial control systems, and more. Ensuring security with robust password management policies is key, and utilizing enterprise password management software, such as the WALLIX Bastion Password Manager, significantly simplifies this daunting task.
Cost of a Data Breach vs. Cost of a Security Solution
You can’t spend your way into a strong security posture. Being secure involves integrating tools, policies, people, and budgets. Getting secure will absolutely require some expenditure of cash. How much is the right amount? The answer depends on each organization’s unique security needs. In general, though, the best practice is to assess the potential financial impact of an incident (data breach cost) and weigh it against the cost of staying secure through breach prevention. Figuring this out can be a bit challenging, but it can be done.
How PAM Enables IEC 62443 Implementation
The IEC 62443 standard is a sprawling, highly complex collection of cybersecurity standards addressing the unique needs of Industrial Automation and Control Systems (IACSs). It covers the full spectrum of security, from risk analysis through the definition and implementation of security policies for IACSs. As with most security standards, the issues of user access control and identity management are critical to success. In particular, an organization seeking to be certified for complying with the IEC 62443 standard should address the matter of Privileged Access Management (PAM). PAM relates to administrative, or privileged, users who can set up or modify the IACS elements that are being secured through the standard.
Uniting Identity Access Management (IAM) and PAM for Cohesive Identity Governance
This month marks the 25th anniversary of the famous “On the Internet, no one knows you’re a dog” cartoon appearing in The New Yorker. Oh, how true that was, and still is, a quarter century later. Chances are, artist Peter Steiner had no idea how prescient his drawing was. We are indeed in the Internet dog days, of identity access management (IAM) and PAM at least.
The Critical Elements of a Scalable PAM Solution
An organization’s security posture benefits from the ability to manage and track access to privileged accounts. Privileged users—as well as those impersonating them—can present major security threats. A Privileged Access Management (PAM) solution offers an answer. It enables security teams to stay on top of privileged account access. To work, however, it must be a scalable PAM solution. The PAM solution must scale flexibly in a growing organization or suffer being disused, to the detriment of security overall. What does it take to build a scalable PAM solution? This article explores the answer to that question.
What is Insider Threat?
In the cybersecurity industry, we often talk about the ‘Insider Threat’ that organizations face in security their most critical data and assets. From manufacturing to healthcare, every business encounters the challenge of both preventing and detecting these risks. But what exactly is Insider Threat? What does it mean for business?
Supply Chain Management and Supply Chain Security: Addressing Vulnerabilities with PAM
Supply chains are essential for the proper functioning of industrial systems and critical infrastructure. However, they’re also quite messy, in terms of security. Supply chains invariably connect users and systems from multiple entities, often in different countries. This setup exposes every company in the supply chain to cyber risk. Among countermeasures, Privileged Access Management (PAM) offers one of the best ways of minimizing supply chain vulnerabilities.
Controlling Privileged Access for Telecommunications & Cloud Service Providers
As cybersecurity concerns rise across all industries, as media and service companies, Telecommunications and Cloud Service Providers (CSPs) face particular challenges. With massive amounts of client data and critical infrastructure, they are tempting targets for hackers. Telecom and CSPs need security solutions that can adapt and evolve with them, and respond to challenges unique to their industries.
Privileged Account Security Solution | Understanding Privileged Account Security
All eyes on us: 4-Eyes Session Monitoring
IT security has never been so important, as hacks and data breaches are at an all-time high (and climbing). When it comes to the security of your data and infrastructure, visibility and control are paramount. You can put in place all manner of corporate policies and password rules, but oversight of administrator actions and the ability to review past activity are paramount for both peace of mind and compliance with stringent cybersecurity regulations.
SCADA Security and Privileged Access Management (PAM)
Industrial plants and power utilities commonly employ the well-established Supervisory Control and Data Acquisition (SCADA) framework to manage their Operational Technology (OT) systems. In recent years, SCADA’s cyber risk exposure has increased with the advent of the Internet and the IP-enabling of traditionally isolated SCADA system elements.
PAM to the Rescue: 3 Common Security Scenarios
Despite the globally-increasing threat of cyber attack, and what feels like near-daily major news reports of data breaches in our most sensitive industries, many companies still under-value cybersecurity. While the data breach fatigue is real, organizations from every sector need to ramp up their IT security practices.
Cybersecurity Simplified: Security is Nothing Without Control
When talking about Privileged Access Management, it’s important to focus on the real objective: to ensure that only the right person can access the right system at any given time. A password vault can easily handle that, but you really need more. It’s far more important to ensure that when someone accesses a target, this person does only what they are supposed to do, and nothing more.
Privileged Access Management Strategy | Devising an Effective PAM Strategy
Security managers today understand they need to either implement or upgrade their Privileged Access Management (PAM) programs. The role of privileged account abuse in many recent, serious cyberattacks reveals just how important this aspect of security has become. Success, it turns out, involves more than just acquiring a PAM solution and installing it.
Agile Regulatory Compliance | Webinar
Staying agile is crucial in a fast-paced world. Businesses need to move quickly to stay ahead of their competition and react immediately when faced with (cyber) threat. Business processes need to be flexible to allow room for growth and evolution in the needs and shape of the organization.
12 IT Security Questions You Should Be Asking
When it comes to the IT security of your organization, you don’t want to leave anything to chance. These days, the vast majority of businesses worldwide are subject to cyber attack (upwards of 89%, in fact). You can’t risk making it any easier for your critical data to be accessed and stolen.
Robust Privileged Identity Management Using Session Management
Ensuring security across organizations is complicated. Between securing the perimeter, enforcing password policies, and attempting to stop breaches before they occur, there is a lot that needs to be considered. Implementing robust privileged identity management through advanced session management tools is one of the key steps to improving organizational security.
New Rules for Privileged Access Management (PAM)
After a trying day at the Security Operations Center (SOC), a Privileged Access Management (PAM) super-admin just wants to have a nice cup of tea and a few minutes relaxing in front of the television before turning in for the night. But, as he dozes and slips into an InfoSec fever dream, he desperately seeks entertainment, flipping through the channels, returning again and again to the classic “New Rules” segment of “Real Time with Bill Maher.”
Compliance Deadlines: GDPR, NIS Directive & Future Cybersecurity Regulations
Time’s up! Cybersecurity compliance is no longer optional for global businesses as IT standards and regulations increase at both state and industry levels, worldwide.
IGA and PAM: How Identity Governance Administration Connects with Privileged Access Management
Misappropriation of user identity is one of the root causes of many serious cybersecurity incidents. The threat can appear as a malicious actor impersonating an authorized system user, a hacker creating a fictitious user account, or a legitimate user taking improper actions. In each case, security managers may have trouble detecting the actions of an ill-intentioned user or they discover the problem after the fact.
Cyber Insurance | Protect Your Business Against Cyber Attacks with PAM
While the modern business world becomes ever more digital, the need for insurance remains consistent across time. Lloyds of London, for instance, dates to the 17th century, building a global reputation for meeting the ever-changing requirements for insurance.
Unlike the 17th century, however, today’s demand is for cyber insurance.
With digitized business processes and data migrating to the Cloud, IT security is the biggest challenge organizations face, with a need to defend against data theft and other cyber-crime in an increasingly digital economy.
Privileged Access Management (PAM) for MSSPs Using AWS
Amazon Web Services (AWS) present a good news story for service providers, but security challenges remain. AWS gives service providers a way to grow their businesses without having to deal with many of the hassles and costs of maintaining a cloud infrastructure. A Managed Security Services Provider (MSSP), for instance, can let AWS do the heavy lifting for them, supplying an essentially infinitely scalable infrastructure.
The CISO’s Guide to Security Compliance (with PAM)
With major data breaches flooding the news and high-stakes security regulations coming into effect (looking at you, GDPR and NIS Directive), CISOs worldwide are scrambling.
Azure Security Monitoring and Privileged Access Management (PAM)
Microsoft Azure offers broad, exciting new capabilities for enterprise IT. The new Azure IoT Hub, which enables large-scale deployment of Internet of Things devices, is just one example. The IoT Hub, however, presents a number of challenges, such as security monitoring on Azure.
Test your Cybersecurity Skills: Take the Quiz!
Did you know that the greatest threat your organization faces is from your own privileged users? Intentionally or not, employees and 3rd-party providers with privileged accounts represent your most significant vulnerability to cyber attacks.
Why Retailers need Privileged Access Management | PAM for Retail
Cybersecurity is a growing issue for businesses worldwide, as the data they handle becomes more and more significant and the threat of a breach more imminent. Nowhere is this challenge more evident than in the Retail sector, where systems are widespread and consumer data handling is constant.
Cloud Password Management with PAM
Confidence in cloud security is growing. According to the Ponemon Institute’s 2018 Global Cloud Data Security Study, the percent of IT managers who feel that it is difficult to secure confidential or sensitive information in the cloud has fallen from 60% in 2016 to 49% today. That trend notwithstanding, many in the industry still feel cloud security is difficult to achieve. The same study reveals that 71% of IT managers believe is more difficult to apply conventional information security in the cloud computing environment, while 51% think it is more difficult to control or restrict end-user access.
Will you survive your next security audit?
A security audit is something that every single company with an internet connection, and that handles customer/individual data should be concerned with. Without elaborating more than necessary, recent regulations makes it, if not mandatory, at least strongly recommended to audit your IT security to ensure compliance.
Picking a PAM Solution
Imagine a hacker is lurking inside your network. Indeed, it’s likely a few malicious actors are already inside your domain despite your best efforts to keep them away. Now, imagine the hacker stealing the credentials of a trusted system administrator. With the back-end access permitted to this privileged user, imagine the kind of damage the hacker can do.
WALLIX at RSA Conference 2018
You’ve seen us in Belgium… you’ve seen us in Abu Dhabi… Now find us in San Francisco at RSA Conference 2018!
Addressing MSSP Cybersecurity Challenges with Privileged Access Management
Outsourcing of security is on the rise. The MSSP business grew into a $9 billion category in 2017, and Gartner reports that over 50% of organizations will be outsourcing some or all of their security work to Managed Security Service Providers (MSSPs) by next year.
Strengthening Cyber Resilience Through Privileged Access Management
Cyber resilience refers to how well an organization can recover from a cyber incident. Many factors contribute to success with cyber resilience, but any attempt to achieve cyber resilience should prominently feature Privileged Access Management (PAM).
Cyber Interview: SPAM Email and GDPR
While SPAM email has been flooding our inboxes for many years now, what do we really know about who’s sending them and where they come from? And how is SPAM impacted by the upcoming – and increasing – data privacy and security regulations states are implementing worldwide?
Improving Cloud Security Using Privileged Access Management (PAM)
More and more organizations are making the jump to the cloud in an effort to simplify IT and business management. Although this move can make it easier for organizations to scale operations and have more agility to evolve based on the market, it leaves them vulnerable to an ever-growing range of cyber threats. In order to reap the benefits of utilizing cloud environments while protecting organizations from attack, teams need Privileged Access Management (PAM).
Facing the Global Cybersecurity Skills Shortage
How do you beef up cybersecurity if you can’t find qualified personnel to take on the task? This is the question many organizations are asking the world over as a result of a global shortage of cybersecurity skills.
Thought Leaders Speak: Be secure by combining simplicity with a robust cybersecurity solution
“Simplicity is the ultimate sophistication.” ~ Leonardo da Vinci
Take it from Leonardo (Not DiCaprio. The other one.) Simplicity makes a work of art that much more sophisticated and beautiful. The same is true in technology. Simplicity is elegant. Simplicity sells. Simplicity also makes for effective security. Indeed, the IT world has only grown more overwhelming since the noted security expert Bruce Schneier remarked in 2001, “Complexity is the enemy of security. As systems get more complex, they get less secure.”
Countdown to the NIS Directive: The Challenges of Compliance
With everyone’s minds focused on the upcoming GDPR deadline, EU members must not overlook the NIS Directive. EU member states must implement measures to comply with the NIS Directive before the 9th of May, 2018. So what are the biggest challenges to compliance with the directive?
Meeting Compliance Regulations Using Privileged Access Management (PAM)
Cybersecurity is a top concern for organizations across the globe. As a result, more and more compliance regulations and laws are being put in place, but meeting these strict rules can be a challenge for organizations. In some cases, security teams may need to comply with multiple regulations based on their geographic location. They need a way to meet compliance without interrupting operations or impacting day-to-day tasks.
Implementing the NIST Cybersecurity Framework with PAM
The National Institute of Standards and Technology (NIST) publishes the Framework for Improving Critical Infrastructure Cybersecurity.
WAB is dead, long live the Bastion 6.0
New year, new version for the long-awaited version: the Bastion 6.0.
Privileged Access Management Features | PAM Features
Privileged access management (PAM) helps you maintain control and visibility over your organization’s most critical systems and data. It includes numerous tools and features that can help deter and prevent data breaches caused by both malicious insiders or external cybercriminals.
PAM | The Benefits of Privileged Access Management
Data breaches are occurring at an ever-increasing rate. More and more businesses are feeling the devastating impacts of breaches.
Is There Such a Thing as Simple and Robust Cybersecurity?
Is there such a thing as simple and robust cybersecurity? Do we face an inevitable choice between simplicity and robustness? If we want one, do we automatically lose the other?
The Cyber Interview: Keys to reinforcing security by design
During an earlier interview on the challenges relating to security by design and connected objects (IoT), Julien Patriarca, Professional Services Director at WALLIX and cybersecurity expert for more than a decade, tackled the issue of responsibility with regard to security.
The Cyber Interview: Security by design and the IoT — who’s responsible?
As digital technology and the Internet undergo constant change, users’ habits shift along with them, magnifying as a result their demands for speed and availability on the objects and tools that they use on a daily basis. But, the rush to digitalize everything to make life easier turns the spotlight on the challenges of cybersecurity in digital technology.
Cybersecurity Trends and Cybersecurity Market Insights for 2018
Buckle up! If the expert forecasts are correct, 2018 is going to be quite a ride for cybersecurity professionals.
Access Management Platform | WALLIX Access Manager
Benefiting from an Access management platform is a key component of a comprehensive cybersecurity strategy.
Reducing the Cost of a Data Breach with Privileged Access Management (PAM)
If the 19th century poet Elizabeth Barrett Browning had been asked about cybersecurity, she might have written, “How does a data breach rack up costs? Let me count the ways.”
Worried about breaches? You need a privileged session management suite
More than ever before, organizations are getting attacked from all sides. Between malware infested emails and stolen credentials, companies are seriously threatened.
ICS Security | Using PAM for Industrial Control Systems Security
Industrial control systems (ICS) are critical to numerous industry operations and have become high-profile targets for cybercriminals who may infiltrate ICS to cause damage to the systems themselves or use the systems to gain access to other parts of a corporate IT infrastructure.
Understanding the Uber hack with Privileged Access Management (PAM)
- The data of 57 million users has been stolen from Uber.
- Malicious intruders managed to gain access to a GitHub private coding site used by some Uber software engineers, find AWS credentials, and use them to steal private data.
SSH agent-forwarding: going barefoot (socket-less)
Would you really wear sockets with flip flops to walk on a nice sandy beach? The same thing goes with SSH agent-forwarding: using a socket can sometimes be inappropriate.
PAM for Financial Services: Preventing Cyber-Attacks in Finance
All organizations understand the need to have strong cybersecurity measures in place to protect personal and corporate data. Financial services, in particular, have an increased need for advanced security with both money and personal data at risk.
ISO 27001: Understanding the Importance of Privileged Access Management (PAM)
We recently published a paper about the role of Privileged Access Management (PAM) in the ISO 27001 standard. ISO 27001 is the world’s most comprehensive and recognized Information Security Management System (ISMS) framework.
Gartner Market Guide for Privileged Access Management Report: WALLIX Recognized as a Representative Vendor
Privileged access management (PAM) is becoming an increasingly important aspect of security infrastructure for organizations of all sizes. Many recent breaches including the Equifax breach and Deloitte breach could have both been prevented if these organizations had a PAM solution in place.
PAM, SIEM, and SAO: Leveraging Cybersecurity Tools to Move the Needle on Alert Management
Every cybersecurity operation is like NORAD, the command post where the US Air Force “opens up one eager eye, focusing it on the sky…” as the German singer Nena put it in her 1980s classic “99 Red Balloons.” Instead of watching for 99 red balloons, we’re looking at alerts, an endless, massive flood of security alerts—more than 10,000 per day for most organizations.
CIS Critical Security Controls: The Role of PAM
The Center for Internet Security (CIS), the non-profit whose mission is to "enhance the cyber security readiness and response of public and private sector entities,” publishes “The CIS Critical Security Controls for Effective Cyber Defense.”
Deloitte Breach: A Lesson in Privileged Account Management
Another day, another major data breach uncovered at a high-profile company. Deloitte has recently announced that malicious outsiders infiltrated their email database and gained access to everything it contained, including confidential emails, attachments, IP addresses, login information, and more.
The right way to SUDO for PAM
SUDO or NOT SUDO. In the PAM industry, both sides have many supporters and with arguments such as: “It’s free but it’s not maintained”. As usual, there is no right or wrong answer, but there is a right way and a wrong way to secure your systems.
SWIFT Framework: SWIFT security and PAM
The Society for Worldwide Interbank Financial Telecommunication (SWIFT), the global banking information network, facilitates over $5 trillion in bank transfers every day. It therefore presents an extremely high value target for cyber-attackers.
Maintaining Visibility Over Remote Access with Session Management
Remote access is no longer an “option” for organizations, it is a necessity for both IT and business operations. Remote access is required by your own employees and third-party service providers like software vendors, support teams, and consultants.
Equifax Breach: Preventing Data Breaches with Privileged Access Management
The Equifax Data breach is one of the largest and most impactful data breaches over the last few years. The breach gave hackers access to over 143 million records.
WALLIX Bastion: New Product Offerings
Protecting critical data and systems is a fundamental component of any enterprise or SMB (small and midsize business) security strategy. The best way to protect your organization is by ensuring the security of privileged user accounts using privileged access management (PAM).
Session Manager | What It Is and Why You Need It
A session manager works in conjunction with an access manager and password manager, to ensure that critical information is only accessible to specific users.
Privileged User Monitoring: Why Continuous Monitoring is Key
Understanding what is going on within your organization’s network is a critical component of strong security operations.
The Dangers of Privilege Escalation
Threats no longer originate just from your network perimeter – the majority of cyberattacks today are due to privilege escalation that occurs inside the heart of your systems where your precious data lives.
Privileged Access Management Best Practices
Privileged access management (PAM) is imperative in protecting critical systems and data. Organizations can’t just rely on perimeter-based defenses; instead, they must maintain complete control and visibility over privileged users and their access to various resources to ensure security.
Cybersecurity Framework: Meeting NIST SP 800-171 Compliance Regulations
NIST SP 800-171, the Special Publication from the National Institute of Standards (NIST) sets requirements governing how Federal government contractors must protect Controlled Unclassified Information (CUI) hosted in nonfederal information systems and organizations.
Preventing Data Disasters with a Privileged Session Manager Solution
Organizations need to support the activities of a wide range of end-users, including third-party vendors, contractors, temporary employees, and more.
Enable secure application-to-application communication
I am not just a standalone application, I also need to communicate with my peers!
Maintaining Data Integrity with Privileged Access Management
Without the proper security solutions in place like monitoring and access management, your organization’s data integrity could be at risk.
ICS Security: Russian hacking Cyber Weapon Targets Power Grids
A newly developed Russian hacking cyber weapon has the potential to disrupt power grids and cause major blackouts around the world.
IAIT review: The WALLIX Bastion leaves remarkably good impression
Independent German institute IAIT puts WALLIX to the test: WALLIX ADMINBASTION SUITE 5.0.2 leaves remarkably good impression
The first step evaluated was the integration capacity of the Bastion which is complemented by an assistance configuration guide.
Privileged Access Management: Going Beyond the Perimeter with IDC
International Data Corporation (IDC), the leading provider of market intelligence, advisory services, and events for the IT industry, has partnered with us to report on the importance of privileged access management (PAM) for security infrastructures in all industries.
The Cyber Interview: The Challenges of Cloud Security
As companies move to the Cloud, new security issues are emerging. Between the scope of state-of-the-art practices and new uses, our expert provides an update on Cloud security.
Privileged Access Management Use Cases: Protect Your Organization
Privileged access management is an important part of the security infrastructure for all organizations.
Why do you need to build (AD) bridges when there is already a Highway?
Integration between several worlds (Windows; Unix/Linux etc.) often requires several adapted tools. This relates to AD Bridging integration.
Threat Intelligence and Privileged Access Management
Threat intelligence helps a cybersecurity team prioritize its work by focusing on the most serious threats. In tandem, Privileged Access Management (PAM) strengthens the controls devised to counter such serious threats.
WALLIX and Schneider Electric strengthen industrial systems security
Since industrial systems are increasingly connected to information systems for production management, planning, and remote access matters, security issues are spreading throughout industrial computing.
Privileged Account Security Handled with PAM
Privileged access management (PAM) is the solution your organization needs to manage all accounts and ensure privileged account security .
A Cybersecurity Ecosystem Is the Key to Great IT Security
IT security has long experienced a tension between point solutions and integrated solutions. As threats grow more serious, complex and frequent, however, we see many of the most forward-thinking organizations adopt a more unified approach.
Health IT Security: Supervise Users with Privileged Access Management
Privileged access management helps your health IT security team manage and audit the activities of all privileged users.
The Bastion secures your applications with AAPM
The WALLIX Bastion offers AAPM (application-to-application password management) with a fingerprinting proprietary technology to authenticate third party applications.
The Role of Privileged Access Management in Industry 4.0
Industry 4.0 puts capabilities like interoperability, data transparency, and autonomous cyber systems into the service of industrial operations. The trend relates to cyber-physical systems, cloud computing and, the most pervasive of them all – the Internet of Things. Its openness, self-directed and interconnected nature creates new security challenges. Privileged Access Management (PAM) solutions can play a key role in reducing the risk.
PAM as a State of the Art Security Tool
Security teams already equipped with SIEM and IDS can go further with Privileged Access Management (PAM), a state of the art security tool that enables auditable logs of administrative sessions.
SOX and Privileged Access Management
Sarbanes Oxley… aka “SOX.” Wow, is that still a thing? Oh, yes, you can bet your 10K on it. The law requires publicly traded corporations to document, implement, audit, and certify internal controls over financial reporting. This includes a great deal of attention to IT controls and policies. Access controls are critical for SOX. As a result, SOX and Privileged Access Management (PAM) are closely linked, or should be.
Privileged Access Management and Vulnerability Systems: Qualys and WALLIX
Complexity is the enemy of cybersecurity. Yet, it can’t be avoided. Even a relatively small organization will have multiple people operating and administering multiple IT assets while fending off multiple threats. Any problem is basically a problem cubed. How do you keep things secure in that environment?
GDPR and Privileged Access Management (PAM): What International Businesses Need to Know
The European Union is on the verge of enacting its new privacy regulations, known as the General Data Protection Regulation (GDPR). Replacing the existing EU data privacy rules, GDPR is simply the latest in a long line of privacy regulations dating back to 1980. While GDPR clarifies and simplifies a number of data protection requirements, it adds new rules that will almost certainly present challenges to international businesses working in the EU.
PAM and Database Security
Structured data is at the heart of virtually every company’s most valuable IT assets. Database security is therefore critical. In this article, we look at how a privileged access management (PAM) solution can improve your existing database security.
Industrial Control Systems Security: An Interview with WALLIX
Industrial Control Systems (ICS) are used to remotely control and monitor a variety of industrial enterprises like manufacturing, electricity, water, oil, and gas. The systems operate mostly on remote commands that are pushed to physical stations and devices. These systems are crucial in controlling and monitoring operations to ensure ongoing operations and safety for the surrounding community.
Preventing Cyber Espionage: Cyber Espionage and Corporate Security
The threat of cyber espionage used to primarily be the domain of defense officials and writers of pulp fiction. No more.
IT Security Productivity
Few people want to talk about the nitty-gritty of IT Security productivity, but the reality is that companies are spending ever-increasing amounts on IT security so productivity is a topic that isn’t going away.
ICS | Industrial Control Systems Security: Regulations
Industrial Control Systems (ICS) are critical systems used in industrial enterprises like electricity, water, oil, gas, and data. ICS operate based on centralized supervisory commands that are pushed to remote stations and devices. These field devices control operations, collect data, and monitor the environment.
Using RSA Authentication Manager for PAM
WALLIX’s Privileged Access Management (PAM) solution integrates with the RSA Authentication Manager and has just received the label RSA Ready.
PAM and the Cybersecurity Plan
In Part One of this two-part series on cybersecurity planning, we covered the basics of what you need in your IT security plan. In this second part, we explore the role of Privileged Access Management (PAM) in security planning.
Elements of an Effective Cybersecurity Plan
A review of the key elements of an effective cybersecurity plan to help security managers prevent or mitigate the impact of a breach.
Cyber Interview: 3 Steps to Implement Privileged Access Management
In the world of cybersecurity, Privileged Access Management (PAM) solutions are increasingly attractive to companies and organizations. PAM solutions help protect their most sensitive data and systems from cyber threats.
But how do you properly implement these solutions? Our cybersecurity expert outlines 3 critical steps to privileged access management in this exclusive interview.
Cloud IT Security: PAM in an Agile World
We are now firmly in the era of agile software methodology and cloud hosting. New incarnations of the agile methodology continue to emerge regularly, promising greater flexibility and economy for the IT department as well as greater strategic agility for the business. But these processes also introduce new risks...
How can we combat threats linked to privileged users?
While cyber threats are increasing in today’s digital world, they are more and more often linked to privileged users. Why is that? What can be done about it? We asked these questions to Julien Patriarca, cybersecurity expert and Support and Services Manager at WALLIX.
ICS cybersecurity: PAM and securing Industrial Control Systems
Industrial entities typically run two parallel sets of information technology systems: Corporate IT and Industrial Control Systems (ICS). Due to the proprietary nature of most ICSs and their unique usage requirements, ICSs tend to have quite different security capabilities from their corporate IT brethren.
PAM and Third Party App Maintenance
Organizations are increasingly outsourcing the maintenance of applications to third parties. Providers of this type of service range from global giants like IBM and HPE to smaller, specialized firms as well as cloud service providers. There is much to like about the idea of having someone else maintain your applications. It is often less expensive than having in-house staff handle the workload. Plus, you don’t have to be concerned with retaining (or losing) application skillsets in your IT department.
Changes in NYDFS Cybersecurity Regulations 23 NYCRR 500
The New York State Department of Financial Services (NYDFS) has just issued an updated version of its proposed Cybersecurity Requirements For Financial Services Companies, known as 23 NYCRR 500. Though these rules may yet still be modified before they become official at the end of January, the consensus is that this most recent draft is essentially final.
Cloud Bastion: WALLIX now on AWS and Azure
In cloud computing, you need a bastion (aka a jumpbox) to provide secure access to your users and outside applications. The bastion is a specialized server that has been hardened against outside attacks and that serves as a gateway for your users.
Calling IT Security Channel Partners!
WALLIX has recently seen a big increase in interest in our channel and reseller programs. This dramatic increase is being driven by several trends:
Enterprise Password Vaults are NOT ENOUGH. You need Session Management
Password vaults are an important part of locking down your privileged accounts. However, they are not sufficient for ensuring either the security or the auditability of those privileged accounts. While password vaults prevent direct root access to your devices, applications, and systems… password vaults by themselves do not provide visibility nor control over privileged user actions. This requires robust session management.
GDPR: A major asset for European companies
When discussing the General Data Protection Regulation (GDPR), two main issues are often raised: the benefits it brings to individuals, or the financial and organisational consequences it has on companies. However, its representing a real key asset for European firms is often omitted.
Service Provider Security: Protect from Disaster, Create Added Value
Embedding the WALLIX Privileged Access Management Solution with Service Providers offerings helps them to create added value and protect them from disaster!
What is an Enterprise Password Vault?
What does an enterprise password vault do?
Why You Want Splunk-PAM integration
Let’s explore the generic advantages of integrating SIEM with PAM, and look at the specific integration of Splunk with the Wallix AdminBastion (WAB) Suite.
Privileged Session Management
Privileged Session Management: What is it?
Privileged session management allows security administrators to monitor, control, and audit work sessions of privileged users. The session manager provides proxy-access to all critical resources and therefore prevents direct access to those resources. A session manager is central to privileged access management (PAM) and is generally integrated with an access manager and a password manager.
23 NYCRR 500: Cybersecurity Requirements For Financial Services Companies
23 NYCRR 500 is coming soon. As in, January 1, 2017. So, get ready.
What is Privileged Account Management (PAM)?
Privileged account management can be defined as managing and auditing account and data access by privileged users.
3 Trends from Gartner’s Latest PAM Report
Gartner, the famous information technology research and advisory company, recently published its 2016 Market Guide that delivers a neutral perspective of the Privileged Access Market. Like everyone, we always look forward to reading what the analysts have to say about the PAM market.
Wallix AdminBastion Suite: a key element in Industrial Control Systems security
For Industrial Control Systems, often described as Supervisory Control and Data Acquisition (SCADA), availability and safety are the two top priorities. However, security has now become a major issue and therefore must not be ignored.
We Are PAM, We Are WALLIX
Privileged Access Management (PAM) refers to a set of technologies designed to mitigate the inherent risks associated with the privileged user accounts of administrators and super-users. By providing full control and visibility of the sensitive, daily tasks of such personnel, an effective PAM solution can greatly reduce the risk of attack, while helping to ensure compliance with the relevant regulatory standards.
Privileged Accounts - Prime Targets At Privileged Brands
It seems the bigger the brand, the bigger the challenge for external threats to win brownie points amongst their peers. External threats are taking up the challenge to break through the perimeter and target highly prized privileged accounts that often exist on networks in unprotected Word or Excel documents. With access to these accounts a compromise becomes that much easier.
Risky business: it’s time to talk about third parties
The number of security breaches attributed to third parties continues to rise – the IRS was hit by a wave of attacks last year and let’s not forget the infamous Target breach of 2013 that saw 40 million debit and credit card details leaked - yet a PwC Global State of Information Security Survey found that 74% of companies do not even have a complete inventory of all third parties that handle personal data of their employees and customers, are completely unaware that they’re over-sharing data and often don’t even know who officially “owns” the third party relationship.
Identity Theft Resource Center reports 657 breaches
The Identity Theft Resource Center (ITRC) Data Breach report has recently been published. The ITRC have been tracking security breaches in the United States since 2005, looking for patterns, new trends and any information that help the wider community to educate consumers and businesses on the need for understanding the value of protecting personal identifying information.
Vote for WALLIX and win a Harmon/Kardon Onyx Speaker
Wallix are again finalists in the Computing Security Awards nominated in the category of Identity and Access Management Solution of the Year and also our AdminBastion Suite has been nominated for Editor’s choice.
UK sees 14 percent increase in local government data breaches
Despite global IT security spending peaking in 2016 at $81billion which represents a 7.9 percent increase on 2015, local government organisations in the UK have seen a 14 percent increase in the number of reported data breaches. Local government was second only to the UK health sector when measured by the total number of reported data breaches.
SWIFT Network Breach: Was it an inside job?
Back in February 2016, thieves stole US$81m from the Bangladesh Bank with the possible involvement of an insider. No one broke in, no one wore masks or walked into a bricks and mortar building carrying weapons.
The shady truth about Shadow IT
Shadow IT has CIO’s caught between a rock and a hard place, pushed to deliver the required infrastructure for the business to function whilst remaining nimble and innovative to stay ahead of competitors.
The first step toward change is awareness. The second step is acceptance.
With an ever evolving regulatory landscape and with increasingly smart technology at our fingertips, it’s probably time we paused to examine the way we’re doing business. Just because it’s been done a certain way for years, it doesn't mean that’s still the right way. Businesses need to start seeing the bigger picture rather than forever playing catch-up, as so many are guilty of thus far. Breaking the cycle means analysing the threats that businesses can anticipate both now and in the coming months and years, and determining the smartest solution for them.
It’s time for change, and real progress. This article examines how and why it’s coming, whether you like it or not, and how to make it work for your business.
When Trusted Insiders Go Bad
A recent survey conducted by Gartner of 186 participants released in May 2016 exposed that the main motivation of trusted employees and contractors (insiders) leaking privileged information is financial.
Sage data breach highlights insider threat
This week has seen yet another high profile business based in the UK breached, possibly by an insider threat. This time, it’s a trusted business-to-business software provider Sage Group PLC, which provides business management software for accounting and payroll services to companies in 23 countries.
Building A Robust Cybersecurity Culture
There’s no doubt that awareness of information security in corporations has dramatically improved in recent years. Stories of breaches, both internal and external, have filled the media. Where the CEO has been forced to face the music on the evening news, where most people now understand the value of data and the risk of it falling into the wrong hands.
Monsters Are Real, Insider Ghosts Are Too
Insider threats are very real. Hackers are perceived as being faceless guys that wear hoods. The insider is your colleague, your friend a member of your team. Working with third party companies and contractors is a fact of life.
Privileged Access Management and BREXIT
Certain events are so overwhelming that only a touch of humor can keep us from going mad. BREXIT, Britain’s exit from the European Union, is one of them. This decision is likely to have a serious impact on IT security, especially Privileged Access Management (PAM).
Privileged Access Management (PAM) and Moving Operations into the Cloud
"In preparing for battle I have always found that plans are useless, but planning is indispensable.”
Dwight D. Eisenhower
Cloud Security: Making it Work with PAM
As enterprises embrace a mix of cloud and on-premises deployments of key IT assets, they are using PAM for hybrid cloud security.
Are UK Health Service Breaches Being Taken Seriously?
Are the ICO and health service taking data breaches seriously?
Well, frankly, no. And here's why.
Privileged Access Management for Dummies III - PAM & IAM
May The Force Be With You - But More Careful With Your Data
We all take it for granted that when we need them, the Police will help "protect and serve" its citizens. But sometimes, only sometimes, they protect and serve themselves with unauthorised insider information about the citizens they are paid to help.
The Hidden Costs of Using SSL for Privileged Access Management
The Book of Ecclesiastes reads, “Using a dull ax requires great strength, so sharpen the blade. That's the value of wisdom; it helps you succeed.” (10:10) And it may as well work for information security as InfoSec seems to have many areas of practice where we’re busy cutting down trees with dull axes.
GDPR : The CFO Challenge
Here's why you should be paying attention to GDPR. And this will also certainly interest your investors and shareholders...
Another Award for the Trophy Cabinet - We Won!!!
This latest award refinforces customer feedback and is the second major industry award given to WALLIX AdminBastion Suite in 2016.
Privileged Account Management and BYOD: PAM for Dummies Part II
Is that an iPhone in your pocket or are you just happy to be reading about the security consequences of Bring Your Own Device (BYOD) policies?
Welcome to the second installment of our “PAM for Dummies” blog series.
Acer Computer Maker Gets Aced By Hackers
It’s all too familiar, another day another breach. And this time, it's computer manufacturer Acer which will pay the costs...
InfoSecurity 2016 - Now The Dust Has Settled
Now that the dust has settled and we have a chance to breathe again after what was a tremendously busy event for WALLIX, we can take a step back and review some of the really exciting engagements we had with companies from across Europe with a primary interest in Privileged Access Management.
Privileged Access Management for Dummies: PAM Definition
The first in our PAM for Dummies series, this article offers a business-oriented definition of Privileged Access Management (PAM), an important technology for security and compliance, and how to implement it for robust cybersecurity in your organization.
The Psychology of the Insider Attack - Part II
It’s an uncomfortable topic, but the truth is that employees present one of the most serious information security threats for every organization.
Compliance: Time for Companies to Raise Their Games
‘Governance, risk and compliance’. Three words that are the stuff of nightmares for senior managers. Not because they have done anything wrong, but because the breadth and scope of this area continues to grow exponentially.
Left A Job? Handed Back All of Your Employers Data?
In our daily lives, we all commit our souls signing a contract of employment. Whether an employee or a contractor, similar rules apply when it comes to respecting company data and the associated data policies.
If A Data Leak Can Happen To Google - What Chance For The Rest Of Us?
A few weeks ago, Google’s employee details were leaked by a third party company. Although this was an innocent error, it’s worth considering how much worse it could so easily have been?
The Psychology Of The Cyber Criminal - Part I
We live in an age in which many if not most crimes involve a computer at some point, but we still know very little about cyber criminals and what makes them tick.
The Best Privileged Access Management is the one with 100% Utilization
Privileged Access Management (PAM) can only work when it is consistently and ubiquitously in use. If system administrators either can’t or won’t use a PAM solution, security risks multiply. So do costs. When it comes to PAM, the best privileged access management is the one that gets consistently used.
HM Government Breaches Survey 2016 - A WALLIX Opinion
Cybersecurity in the headlines. Again…
The Wallix Approach to Advanced Persistent Threat (APT)
Many organisations are upgrading their firewalls to stop APTs but this only offers protection from external attacks and internal traffic routed through the trusted zones.
How IT Security Teams can benefit from Privileged Access Management
As an IT Security Manager, the breath of this central role is broad and continually changing.
Compliance - A route to better your business
Really, though…
Today in business, digital storage, communication and transporting data across borders are the norm and we’re seeing an increase in regulation and compliance in various forms.
The High Risk Access Management Solution to help IT Operations
Being head of IT Operations in a mid-sized or big enterprise is becoming a more and more demanding challenge.
Is Your Business Prepared For a Ransomware Stick-up?
Countless Victims
Ransom notes aren’t written with cut out newspaper letters anymore, but in computer code.
General Data Protection Regulation: May Day, May Day
Well, the 5th to be precise, but here’s why you should be panicking…
SOX Compliance. It’s Not Just Another US Thing
It feels like every week there are fresh headlines about hackers bringing organisations to their knees, and such stories always seem to be front-page news. In 2002, following a wave of high profile financial scandals driven by fraudulent accounting practices involving major US corporations including Enron, the heat was such that the government introduced the Sarbanes Oxley Act, or the SOX Act, in an attempt to restore investor confidence. Cyber-attacks have forced us to change the way we do business, and organisations must now take greater responsibility for cyber security and report cyber breaches. This is both an important and positive step because it enables government agencies to strengthen security and allows individuals to mitigate harm, but it’s only a good thing for your business if you’re prepared…
What is Privileged Access Management (PAM)?
What is Privileged Access Management?
The key is to understand the significance of the word “Privileged.”
A privileged user is someone who has administrative access to critical systems. For instance, the individual who can set up and delete email accounts on a Microsoft Exchange Server is a privileged user. The word is not accidental. Like any privilege, it should only be extended to trusted people. Only those seen as responsible can be trusted with “root” privileges like the ability to change system configurations, install software, change user accounts or access secure data. Of course, from a security perspective, it never makes sense to unconditionally trust anyone. That’s why even trusted access needs to be controlled and monitored. And, of course, privileges can be revoked at any time.
Why take extra steps to protect your biggest asset, your data
Getting smarter about information security
Cyber attacks are fast becoming one of the greatest risks of doing business and your chances of being exposed to one are ever growing.
Cyber Attacks: When disaster strikes
Are you prepared for a cyber attack?
…you’ll need to be prepared. And the alarming fact is that when it comes to cyber attacks, most companies aren’t.
Software vs. Consultants in Privileged Account Management
It can be daunting to manage security for privileged accounts. You demand system security while administrators go about their work of changing configurations, installing software, changing user accounts and so forth.
Passwords & Insider Threats: The Threshold For Compromise is Shrinking
Here at Wallix, sometimes we like to look back at what were hot topics and see what has changed or even improved. Just over a year ago, we looked at how insider’s passwords were available for as little as $150.
Would You Want to Hold the Record for the Most Data Ever Leaked?
When Intelligence Contractor employed as a computer analyst, Edward Snowden turned whistle-blower the question was which business or public sector organisation is next. Of those that we have heard about, all seem to be eclipsed by Panama based legal firm Mossack Fonseca.
Is Security Information and Event Management (SIEM) Enough?
Compliance dictates we need to log everything within scope, we must then review the reports of the logs. Can we really be trusted to look at all of these reports, and if so can we really get anything constructive out of them?
Cyber Insurance: Is Your Information Worth The Premiums?
The scale, frequency and magnitude of cyber-crime is truly alarming and getting worse. Recent highly publicised attacks have served to push the issue much further up the management agenda to the extent that only the foolhardy would now argue that cyber-security is not a board level issue.
Financial implications of Privileged Access Management (PAM)
Privileged users can change system configurations, install software, create or modify other user accounts and access secure data.
After CeBIT 2016: a new era of IT security
CeBIT devoted a great deal to IT security and internal threat management
The CeBIT 2016 rebranded itself as “innovation fair”, but it is no surprise that IT security and human behaviour in the digital world have been major concerns at the former computer trade show. IT security interests have escalated in the past few years and numerous astonishing security breach examples have surfaced.
IT security and private data information traceability: your responsibility
Protecting private and sensitive data information
Today, are there established ways to protect private and sensitive data information within operating systems or IT hosting services?
Privileged Account Management: Deployment Options
If you don’t lock your door, you can’t get too upset if someone wanders in and steals your stuff. Information security holds by a similar rule.
Our Wallix AdminBastion Suite Already Wows IT Experts
It's not often that we use our own blog to blow our own trumpet, but when an internationally renowned magazine - which bills itself as ‘the leading source of specialist information and intelligence' for cyber security professionals worldwide – describes our Wallix AdminBastion (WAB) Suite as representing ‘a new design for an old problem of privileged account access’ and recommends it as a ‘best buy’. Well, we couldn’t resist it!
How to ensure Cloud computing security
The public cloud provider business scarcely existed a decade ago. Now, this type of company is at the forefront of a revolution in IT. It’s a varied industry and one that is still evolving dramatically.
Aligning Organizational Roles with Privileged Access Management
Privileged Access Management (PAM) is usually discussed in the contexts of IT or information security. This makes sense. Precise, auditable management of information systems access is an inherently technical matter.
Privileged Access Management’s Role in HIPAA Compliance
How to prepare for EU Standard General Data Protection Regulation?
The GDPR shows that states in the EU are aware of the risk in the cyber world. Protection of private data and personal information are highly important European values and policy-wise organisations have to get ready for new standards.
Managing Risk of IT Service Providers in Digital Transformation
A side effect of digital integration is the growing use of external service providers. The process seems natural, because today’s IT tasks are so complex that organisations work more efficient by outsourcing certain tasks.
UK treasury committee chair calls on banks to improve IT controls
Andrew Tyrie, the MP who chairs the parliamentary treasury select committee is demanding action on the state of banks’ IT systems, firstly calling for regulators to improve both security and resilience following a string of system failures.
Over 70% of UK businesses now using IT contractors
There is no doubt that one of the main driving forces contributing to the positive outlook for companies in the UK is the way in which technology has been changing both consumer and commercial activity beyond recognition.
Only 1/3 of Fortune 1000 companies have an insider threat program
A survey of chief information officers at Fortune 1000 companies by security and information management firm Nuix has found that whilst insider threat programs inside organisations are becoming increasingly important in combatting today’s cyber threats, this issue may not yet have the attention it deserves.
TalkTalk data breach: CEO can’t actually talk about the hack!
On Tuesday TalkTalk CEO Dido Harding appeared before the Culture Media and Sport parliamentary select committee to answer questions on the recent hacking of customer data from the company.
Finance workers are those most likely to bypass IT security measures
According to new research from network security vendor Palo Alto, one in five working in the finance and insurance sector admitted to ignoring cybersecurity policies.
Bad privileged access management at the "root" of VTech woes?
Kid’s electronic toy company VTech is now at the centre of a storm over a breach of its user database, which worryingly included the details of 3 million child profiles.
Why user experience is at the core of effective privileged access management
We live in a world where the technology we use every single day is engineered to be usable. Our smartphones, set top boxes and social media websites have invested a great deal in user experience.