Here in London the TimeOut magazine is a must read (they also have an awesome blog). One of my favourite weekly features is the hilarious and regularly cringe-worthy: “Overheard in London” #wordonthestreet.
Might your system administrator have a god complex?
[fa icon="calendar'] Apr 13, 2015 10:48:24 AM / by WALLIX posted in Mitigating External Attacks
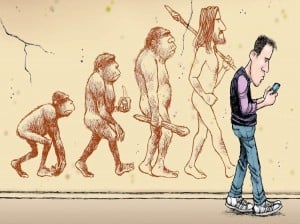
Digital Darwinism: Don’t let access management stop your business evolving
[fa icon="calendar'] Mar 3, 2015 4:58:54 PM / by WALLIX posted in Mitigating External Attacks, WALLIX Products
Recent times are littered with examples of businesses who failed to recognise the changing demands of their consumers and paid a heavy price.
"Privileged Users" top list of insider threat fears
[fa icon="calendar'] Jan 29, 2015 1:11:01 PM / by WALLIX posted in Controlling Third Party Access, Mitigating External Attacks
In this post-Snowden era, we all know that insider threats are becoming a major concern for businesses globally.
IT Contractors: the 3 Pros and Cons
[fa icon="calendar'] Jan 22, 2015 2:57:31 PM / by WALLIX posted in Controlling Third Party Access, Mitigating External Attacks
The IT industry is constantly evolving. This evolution is vital to meet business objectives and drive productivity forward, but it also makes the potential for skills shortages much higher.
5 users who could be your next insider threat
[fa icon="calendar'] Jan 14, 2015 2:06:59 PM / by WALLIX posted in Mitigating External Attacks
Employees are probably the greatest risk facing a business in the modern era, sometimes out of malice, often due to carelessness but always because they have access to information that might be valuable outside your organisation.