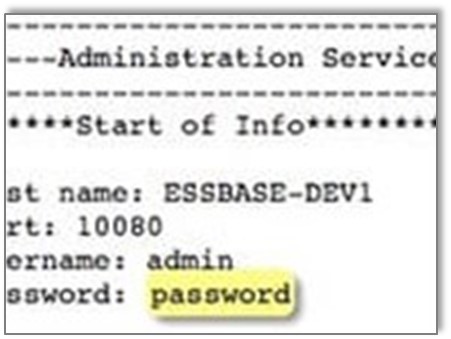
The humble password gets a hard time these days. It seems to be responsible for every hack, data breach or act of cyber espionage that we see reported.
No one likes passwords anymore, but what are the alternatives?
[fa icon="calendar'] Oct 15, 2015 6:06:06 PM / by WALLIX posted in Mitigating External Attacks, Reaching IT Compliance
Work in IT security? Are you ready for cyber insurance?
[fa icon="calendar'] Oct 1, 2015 11:31:09 AM / by WALLIX posted in Reaching IT Compliance, Optimizing Cyber-Insurance
In a report released this week insurance giant Allianz said increasing awareness of exposures and regulatory change would lead to “rapid growth” in cyber insurance.
Could a threat to “business as usual” be a significant risk to your information security?
[fa icon="calendar'] Sep 24, 2015 5:36:11 PM / by WALLIX posted in Mitigating External Attacks, Reaching IT Compliance
This week former Morgan Stanley financial advisor Galen Marsh admitted stealing data from the banking giant. He downloaded a total of 730,000 records to his personal computer from 2011 - 2014.
Are you really reading all those log reports?
[fa icon="calendar'] Sep 8, 2015 3:00:00 PM / by WALLIX posted in WALLIX Products, Reaching IT Compliance
Compliance says that we need to log everything within scope, we must then review the reports of the logs. Can we really be trusted to look at all of these reports, and if so can we really get anything constructive out of them?
What's the aim of every malicious outsider?
[fa icon="calendar'] Jun 29, 2015 1:21:45 PM / by WALLIX posted in Reaching IT Compliance
An IT security professional recently asked me this question. As I began to research opinions and marketing messages it became more clear to me that many in the IT security industry are keen for us to separate the risks posed by a malicious outsider from the exposure created by privileged accounts on the inside of an organization.