If you don’t lock your door, you can’t get too upset if someone wanders in and steals your stuff. Information security holds by a similar rule.
WALLIX
Recent Posts
Privileged Account Management: Deployment Options
[fa icon="calendar'] Mar 16, 2016 3:43:22 PM / by WALLIX posted in Preventing Insider Threat, Controlling Third Party Access
New IT Security Challenges for the Financial world
[fa icon="calendar'] Mar 10, 2016 6:32:14 PM / by WALLIX posted in Preventing Insider Threat, Controlling Third Party Access, Mitigating External Attacks, Reaching IT Compliance
Our Wallix AdminBastion Suite Already Wows IT Experts
[fa icon="calendar'] Mar 9, 2016 9:02:06 AM / by WALLIX posted in WALLIX Products
It's not often that we use our own blog to blow our own trumpet, but when an internationally renowned magazine - which bills itself as ‘the leading source of specialist information and intelligence' for cyber security professionals worldwide – describes our Wallix AdminBastion (WAB) Suite as representing ‘a new design for an old problem of privileged account access’ and recommends it as a ‘best buy’. Well, we couldn’t resist it!
How to ensure Cloud computing security
[fa icon="calendar'] Mar 1, 2016 10:44:13 PM / by WALLIX posted in Preventing Insider Threat, Controlling Third Party Access, Mitigating External Attacks
The public cloud provider business scarcely existed a decade ago. Now, this type of company is at the forefront of a revolution in IT. It’s a varied industry and one that is still evolving dramatically.
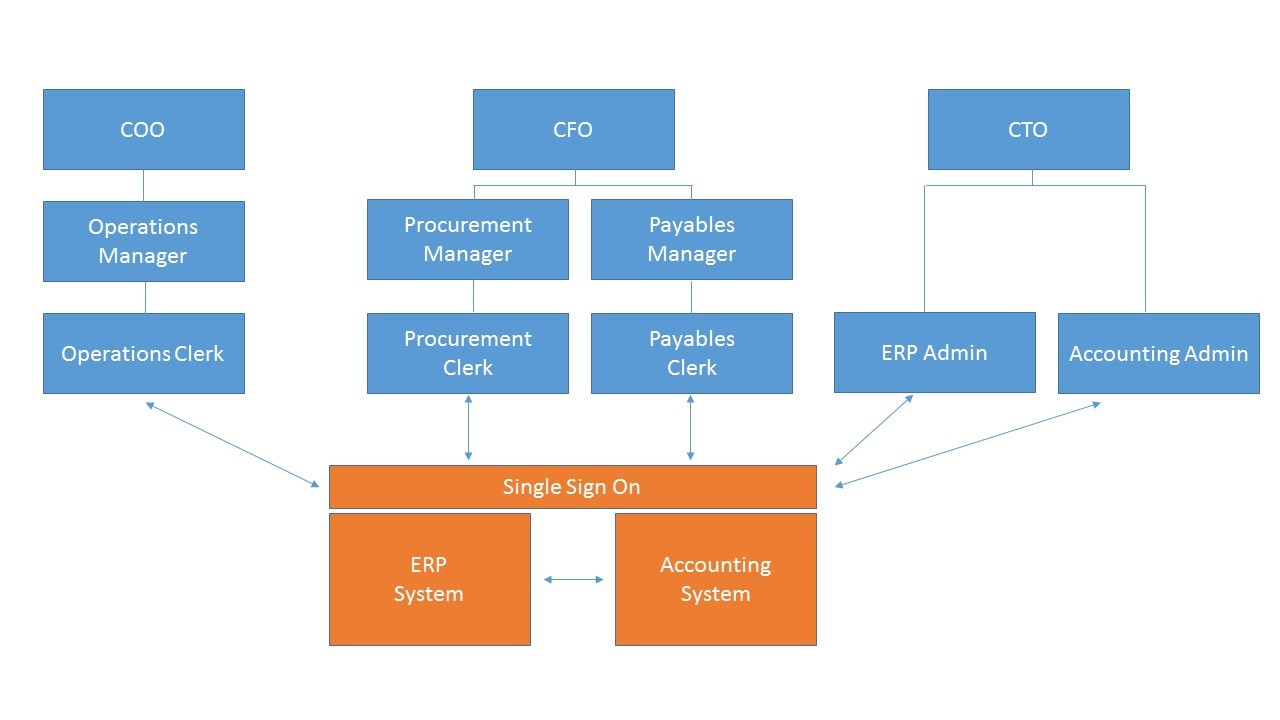
Aligning Organizational Roles with Privileged Access Management
[fa icon="calendar'] Feb 24, 2016 5:06:01 PM / by WALLIX posted in Preventing Insider Threat, Reaching IT Compliance
Privileged Access Management (PAM) is usually discussed in the contexts of IT or information security. This makes sense. Precise, auditable management of information systems access is an inherently technical matter.