Privileged Access Management (PAM) is usually discussed in the contexts of IT or information security. This makes sense. Precise, auditable management of information systems access is an inherently technical matter.
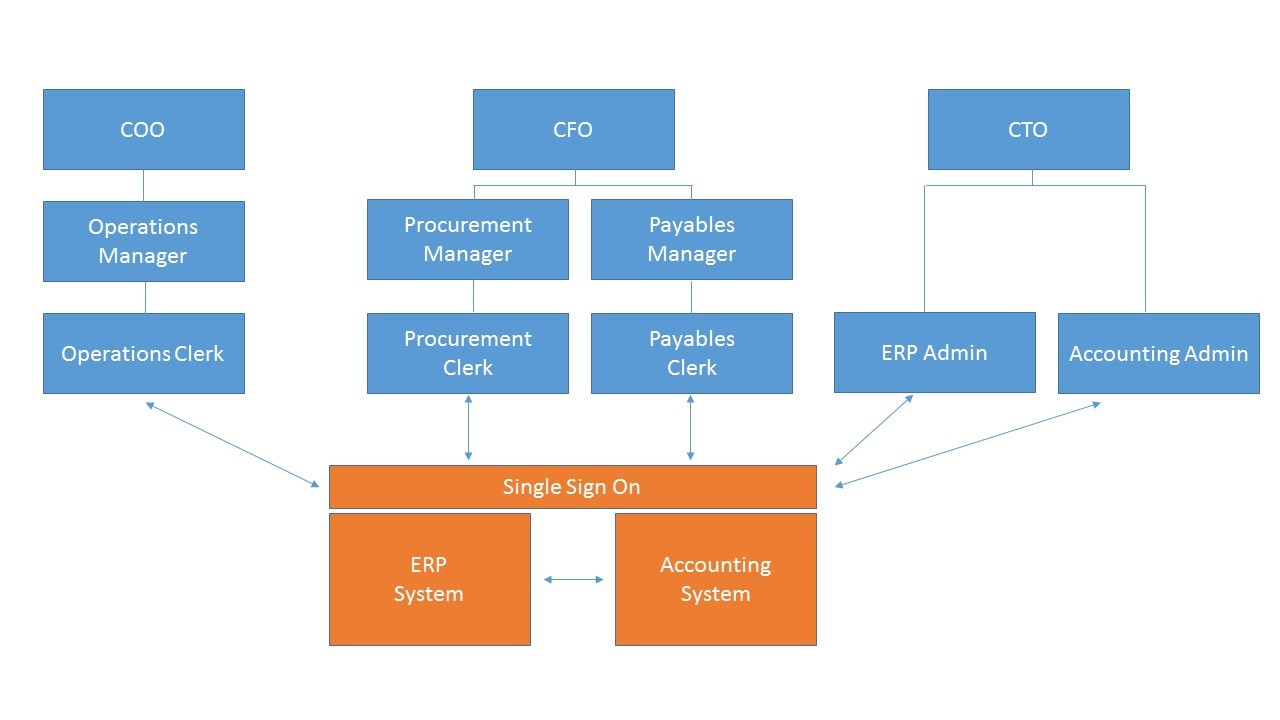
Aligning Organizational Roles with Privileged Access Management
[fa icon="calendar'] Feb 24, 2016 5:06:01 PM / by WALLIX posted in Preventing Insider Threat, Reaching IT Compliance
Finance workers are those most likely to bypass IT security measures
[fa icon="calendar'] Dec 10, 2015 1:17:12 PM / by WALLIX posted in Preventing Insider Threat
According to new research from network security vendor Palo Alto, one in five working in the finance and insurance sector admitted to ignoring cybersecurity policies.
Would you hug a hacker? Why demonising cyber-criminals doesn't help
[fa icon="calendar'] Nov 5, 2015 12:16:12 PM / by WALLIX posted in Preventing Insider Threat, Mitigating External Attacks
In the wake of the Talk Talk hack we heard all kinds of speculation about the motives of these attackers, the methods they might have used and their ultimate goals.
VIDEO: Who are privileged users?
[fa icon="calendar'] Oct 29, 2015 12:48:37 PM / by WALLIX posted in Preventing Insider Threat, Reaching IT Compliance
Managing privileged access is seen as one of the best ways to begin to address the insider threat. But who are these privileged users? And how can you secure them. Chris Pace, Head of Product Marketing for Wallix explains.
IT security: Could you have spotted Snowden?
[fa icon="calendar'] Oct 31, 2014 11:31:00 AM / by WALLIX posted in Preventing Insider Threat
The release of the documentary “Citizenfour”, captures the first interviews with NSA whistleblower Edward Snowden. The Guardian calls the film ”gripping” while the Telegraph says “everyone needs to see it”.