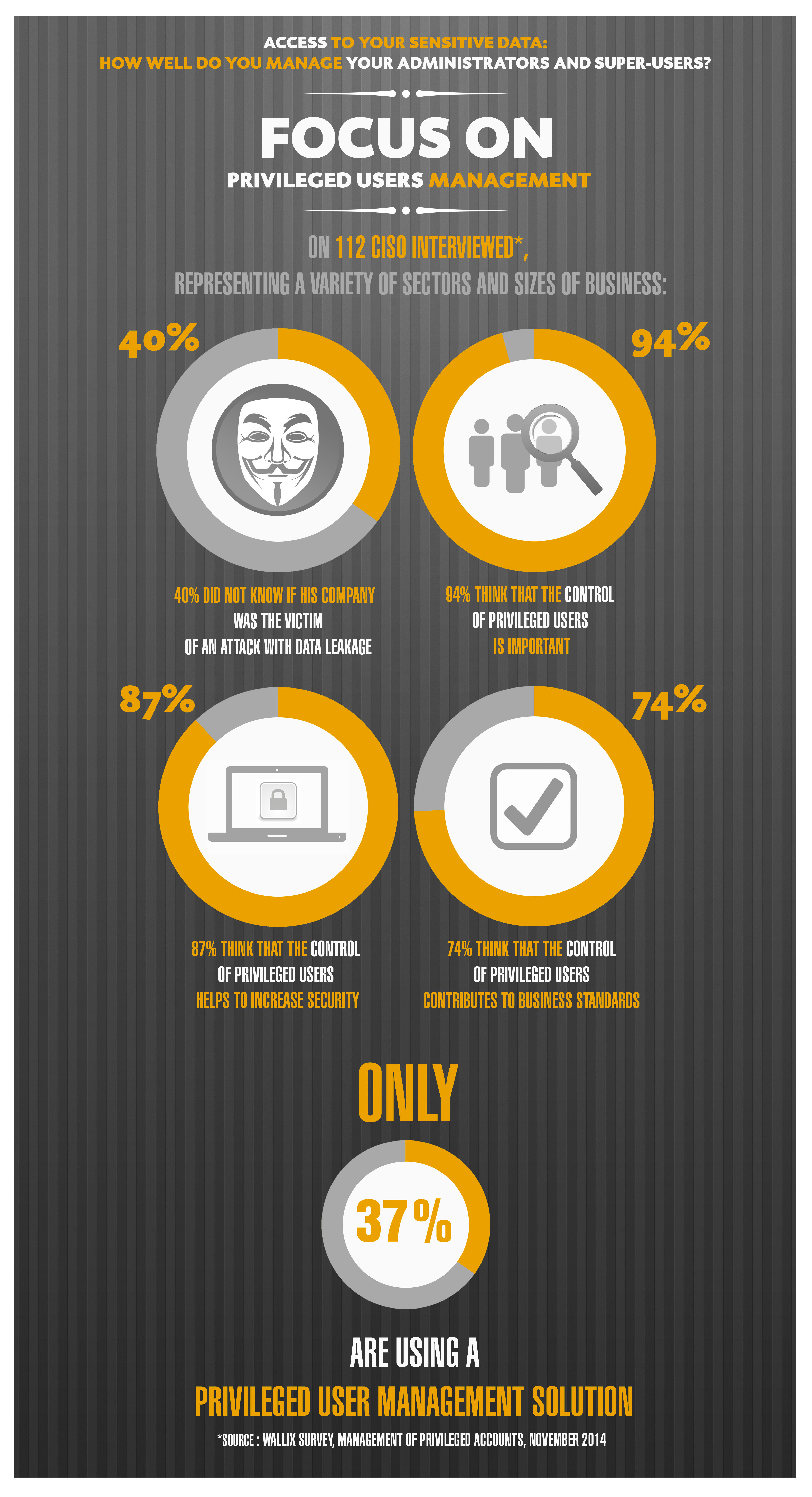
It can be daunting to manage security for privileged accounts. You demand system security while administrators go about their work of changing configurations, installing software, changing user accounts and so forth.
Software vs. Consultants in Privileged Account Management
[fa icon="calendar'] Apr 14, 2016 7:30:00 AM / by WALLIX posted in Preventing Insider Threat, Controlling Third Party Access, WALLIX Products
Passwords & Insider Threats: The Threshold For Compromise is Shrinking
[fa icon="calendar'] Apr 12, 2016 2:57:48 PM / by WALLIX posted in Preventing Insider Threat, Controlling Third Party Access
Here at Wallix, sometimes we like to look back at what were hot topics and see what has changed or even improved. Just over a year ago, we looked at how insider’s passwords were available for as little as $150.
Financial implications of Privileged Access Management (PAM)
[fa icon="calendar'] Mar 29, 2016 3:38:58 PM / by WALLIX posted in Preventing Insider Threat, Controlling Third Party Access, WALLIX Products, Reaching IT Compliance
Privileged users can change system configurations, install software, create or modify other user accounts and access secure data.
After CeBIT 2016: a new era of IT security
[fa icon="calendar'] Mar 24, 2016 10:47:59 AM / by WALLIX posted in Preventing Insider Threat, Controlling Third Party Access, Mitigating External Attacks, Reaching IT Compliance
CeBIT devoted a great deal to IT security and internal threat management
The CeBIT 2016 rebranded itself as “innovation fair”, but it is no surprise that IT security and human behaviour in the digital world have been major concerns at the former computer trade show. IT security interests have escalated in the past few years and numerous astonishing security breach examples have surfaced.
IT security and private data information traceability: your responsibility
[fa icon="calendar'] Mar 23, 2016 10:49:54 AM / by WALLIX posted in Preventing Insider Threat, Controlling Third Party Access
Protecting private and sensitive data information
Today, are there established ways to protect private and sensitive data information within operating systems or IT hosting services?