Privileged users can change system configurations, install software, create or modify other user accounts and access secure data.
Financial implications of Privileged Access Management (PAM)
[fa icon="calendar'] Mar 29, 2016 3:38:58 PM / by WALLIX posted in Preventing Insider Threat, Controlling Third Party Access, WALLIX Products, Reaching IT Compliance
After CeBIT 2016: a new era of IT security
[fa icon="calendar'] Mar 24, 2016 10:47:59 AM / by WALLIX posted in Preventing Insider Threat, Controlling Third Party Access, Mitigating External Attacks, Reaching IT Compliance
CeBIT devoted a great deal to IT security and internal threat management
The CeBIT 2016 rebranded itself as “innovation fair”, but it is no surprise that IT security and human behaviour in the digital world have been major concerns at the former computer trade show. IT security interests have escalated in the past few years and numerous astonishing security breach examples have surfaced.
New IT Security Challenges for the Financial world
[fa icon="calendar'] Mar 10, 2016 6:32:14 PM / by WALLIX posted in Preventing Insider Threat, Controlling Third Party Access, Mitigating External Attacks, Reaching IT Compliance
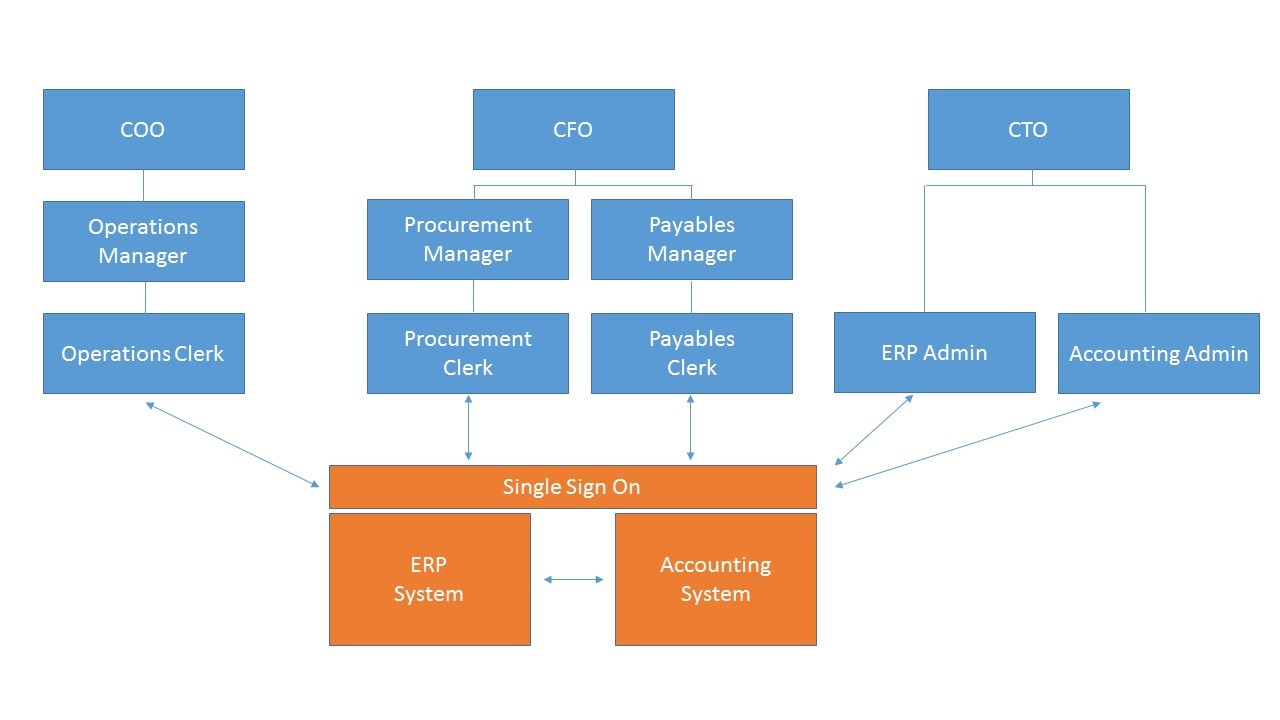
Aligning Organizational Roles with Privileged Access Management
[fa icon="calendar'] Feb 24, 2016 5:06:01 PM / by WALLIX posted in Preventing Insider Threat, Reaching IT Compliance
Privileged Access Management (PAM) is usually discussed in the contexts of IT or information security. This makes sense. Precise, auditable management of information systems access is an inherently technical matter.
Privileged Access Management’s Role in HIPAA Compliance
[fa icon="calendar'] Feb 19, 2016 3:02:56 PM / by WALLIX posted in Reaching IT Compliance